Packet Tracer 5.1 for Windows with Cisco Official tutorials |
- Packet Tracer 5.1 for Windows with Cisco Official tutorials
- CCNA 4 Final
- CCNA3 Final
- BitDefender Total Security 2010 – Proactive Protection Against Viruses, Spyware, Hackers, Spam
- ICND 2 - Nat Sim Question
- CCNA Video Training – 2 Best CCNA Video Training Products Compared
- CCNA Video Training – CCNA Certification Breakdown
- CCNA2 Chapter 10 (NEW)
- CCNA2 Chapter 9 (new)
- How To Become A True CCNA And To Get A CCNA job
- CCNA1 Chapter 8 (new)
- CCNA1 Chapter 7
- CCNA 1 Chapter 6
- 10 Things You Should Know About the Cisco CCNA Security Certification
- Cisco IOS Commands – Using Extended Ping For Network Troubleshooting
- Setting Up Access List On Cisco Router
- CCNA2 Chapter 8 (true 100%)
- CCNA2 Chapter 7 (100%)
- Cisco 640-802 CCNA
- CCNA2 Chapter 6 V4.1 (true 100%)
| Packet Tracer 5.1 for Windows with Cisco Official tutorials Posted: 15 Sep 2009 05:29 AM PDT Cisco has very recently launched the new version of Packet Tracer 5.1. I have uploaded the software with tutorials for the users who are preparing of Cisco exams or improving their network design concepts  Packet Tracer 5.1 Version CODE http://rapidshare.com/files/182507939/PacketTracer_5.1_windows_setup___cisco_official_tutorials_by_heightofglory.part1 of2.rar http://rapidshare.com/files/182486892/PacketTracer_5.1_windows_setup___cisco_official_tutorials_by_heightofglory.part2 of2.rar Packet Tracer 5 Version CODE http://rapidshare.com/files/169210783/Packet_Tracer_5_with_Official_Tutorial_CCNA_v4.0_640-802_by_heightofglory.part1of3.rar http://rapidshare.com/files/169226160/Packet_Tracer_5_with_Official_Tutorial_CCNA_v4.0_640-802_by_heightofglory.part2of3.rar http://rapidshare.com/files/169196881/Packet_Tracer_5_with_Official_Tutorial_CCNA_v4.0_640-802_by_heightofglory.part3of3.rar http://www.mediafire.com/?mimk1gudtyg http://www.mediafire.com/?yzxyjy2lzqz Download 25MB (without tutorials) Download 100MB(with tutorials and labs) Packet Tracer 5.1 is the latest version of Cisco Networking Academy's comprehensive networking technology teaching and learning software. Innovative features of Packet Tracer 5.1, including powerful simulation, visualization, authoring, assessment, and collaboration capabilities, will help to solve problems, and learn concepts in an engaging and dynamic social environment. Donwload Free Certbible, The Most Realistic Practice Questions and Answers,Help You Pass any ExamsPacket Tracer supplements classroom equipment and provides students complementary learning opportunities that are not physically possible to create in the classroom or lab. Packet Tracer 5.1 offers a unique combination of realistic simulation and visualization experiences.PT 5.1 supports the following protocols: HTTP, Telnet, SSH, TFTP, DHCP, and DNS TCP and UDP; IPv4, IPv6, ICMPv4, and ICMPv6 RIP, EIGRP, multi-area OSPF, static routing, and route redistribution Ethernet/802.3, 802.11, HDLC, Frame Relay, and PPP ARP, CDP, STP, RSTP, 802.1q, VTP, DTP, and PAgP | |
| Posted: 14 Sep 2009 07:08 PM PDT 1. A network administrator is asked to design a system to allow simultaneous access to the Internet for 250 users. The ISP for this network can only supply five public IPs. What can be used to accomplish this task? routable translation dynamic translation static translation • port address translation 2. The LAN attached to the Ethernet interface of the Raleigh router shown in the graphic is addressed with private IP addresses. If one public IP is assigned to the company, which commands could be used in a configuration that allows all devices with private IPs in this network to access the Internet? (Choose two.) • ip nat inside source list 1 interface serial0 overload ip nat outside source list 1 interface serial0 overload ip nat inside serial0 • ip nat inside source list 1 pool Raleigh overload ip nat inside Raleigh overload ip inside nat source list 1 interface serial0 Raleigh 3. The command output shown in the graphic was taken from a Cisco 806 broadband router. Which kind of address translation is in effect on this router? static dynamic • overload private public 4. Which of the following IP addresses are defined by RFC 1918 as private addresses? (Choose three.) • 192.168.146.0/22 172.10.25.0/16 • 172.31.0.0/16 20.0.0.0/8 • 10.172.92.8/29 5. How will data be transmitted from the router to the ISP if the router has the two links shown in the graphic? Both links will transmit data at the same rate. 1544 bits can be transmitted simultaneously from the router over the T1 line. • Both links will transmit bits one by one. The 56K link will transmit a maximum of 53 bits at the same time. 6. Which statements about DHCP are true? (Choose three.) DHCP uses TCP. DHCP uses UDP. • DHCP sends messages to the server on port 67. DHCP sends messages to the server on port 68. • DHCP sends messages to the client on port 67. • DHCP sends messages to the client on port 68. 7. Which command would be used to exclude the IP address 192.168.24.5 from the DHCP address pool on a router? Router(dhcp-config)# ip dhcp excluded-address 192.168.24.5 Router# ip dhcp excluded-address 192.168.24.5 Router(config-excluded)# ip dhcp excluded-address 192.168.24.5 • Router(config)# ip dhcp excluded-address 192.168.24.5 Router(config)# excluded-address 192.168.24.5 Router(dhcp-config)# excluded-address 192.168.24.5 8. The WAN connection for a nationwide company with 250 offices must support constant connections to core layer services for file sharing, and occasional Internet access. Which combination of WAN technologies will meet these needs with minimum expense? Frame Relay PVC for Internet access and ATM for file server access Frame Relay PVC for Internet access and ISDN for file server access ISDN for Internet access and X.25 for file server access • ISDN for Internet access and Frame Relay PVC for file server access 9. Which command would produce the output shown in the graphic? show ip dhcp server statistics show ip dhcp binding • debug ip dhcp server events debug ip dhcp binding 10. Which of the following devices is used to establish the communications link between the customer equipment and the local loop for digital lines? terminal adapter modem • CSU/DSU PBX switch ISDN switch Frame Relay Switch 11. Which of the following statements are true about Frame Relay? (Choose three.) Frame Relay operation is defined by a series of ISO standards. • Frame Relay is a packet switched, connection-oriented, wide area network service. Frame Relay only supports point-to-point connections. • A router can be considered as data terminal equipment (DTE) in a frame relay system. Frame Relay is a cell switched, connection-oriented, wide area network service. • Frame Relay networks use a subset of the HDLC protocol to carry information. 12. ITU-T Q.921 specifies the use of which protocol for sending control and signaling messages between the router and the ISDN switch? HDLC IPCP LAPB • LAPD NCP SS7 13. A company needs a WAN connection that is capable of transferring voice, video, and data at a minimum data rate of 155 Mbps. Which WAN connection is the best choice? X.25 DSL • ATM ISDN BRI ISDN PRI 14. Which statement explains why basic DSL is an unpopular WAN connectivity choice for enterprise computer departments that support home users? DSL offers insufficient bandwidth to home users. DSL requires the installation of new cables, which is not always possible for home users. DSL dialup connection time is too slow for business use. • DSL has limited geographical availability. 15. When planning simple WAN connections for a small company, which feature of the three layer hierarchical model makes it a good choice for the WAN topology. It provides for redundancy. • It allows for easy WAN expansion in case of company growth. It is less expensive. It provides faster connection time. It provides less latency and jitter. 16. Which of the following terms describes a device that will put data on the local loop? DLCI CO • DCE DTE PRI BRI 17. Which of the following are supported by a BRI interface on a router? (Choose two.) • Two independent channels that can carry analog data with a bandwidth of 64 KHz. A single 128 Kbps digital bearer channel. Two multiplexed channels carrying digital data. A single 64 Kbps signaling channel. A multiplexed data channel that can only handle SS7 information. • A 16 Kbps delta channel used for signaling purposes. 18. A network administrator has been asked to provide the network in the United States with an ISDN WAN link. The router available to provide the WAN connection is a non-modular Cisco router with two serial connections. What must be done to adapt one of the serial interfaces of this router for the ISDN connection? Nothing. The router is already suitable. Purchase a BRI WAN interface card to install in the router. Purchase a U interface to install in the router. • Purchase a TA/NT1 device to install on the router. 19 (NEED ANSWERS!!!)Which of the following is a function of a DCE device? determines the next-hop address for a packet • multiplexes signals from several sources adapts information for use on a service provider's network used to directly connect two DTEs to simulate a WAN network 20. Why would data frames be discarded in a Frame Relay network? (Choose two.) The frame contains an incorrect IP address. • An error has been detected in computing the frame check sequence. There is not enough bandwidth dedicated for the data contained in the frame. Data is transmitted at a rate greater than the access speed. • The frame contains an incorrect DLCI. 21. Which of the following are commonly used as Data Communications Equipment? (Choose two.) • modem router • CSU/DSU ISDN Switch Frame Relay Switch 22. Which of the following LCP options can be configured for PPP? (Choose three.) • CHAP • Stacker IPCP CDPCP • Multilink 23. Which command will provide for CHAP authentication if the hostname on a challenging router is tampa with a password of florida? • username tampa password florida username tampa florida hostname tampa password florida hostname tampa florida 24. Which of the following describes the PAP protocol? (Choose two.) • sends unencrypted authentication passwords performs a three-way handshake • allows repeated login attempts uses the remote router hostname to verify identity sends a random challenge throughout the session 25. Why was NAT created? (Choose two.) to create firewalls on routers • to conserve IP addresses to translate domain names into IP addresses to map network addresses to the corresponding data link address • to hide internal addresses from external devices 26. An ISDN router is configured for DDR as shown in the graphic to provide Internet connectivity for the company. Immediately after a user in the company attempts opens a web browser to connect to the Internet, another user in the company tries to download a file using FTP. What will happen? (Choose two.) • The user that opened the browser will connect to the Internet because the DDR link will consider this traffic interesting. The Internet user will be disconnected because the FTP data will cause the DDR link to shut down. The DDR link will allow the FTP traffic because it is interesting. The DDR link will not allow the FTP traffic because it is not interesting. The FTP connection will fail because the DDR link is already in use for the Internet connection. • The FTP connection will succeed because the web user already opened the DDR link. 27. Which command configures the SPID on the first B channel of an ISDN interface? Router(config)# isdn spid0 spid-number [ldn] Router(config)# isdn spid1 spid-number [ldn] Router(config-if)# isdn spid0 spid-number [ldn] • Router(config-if)# isdn spid1 spid-number [ldn] 28. What does the command debug isdn q921 display? exchange of call setup and teardown messages PAP and CHAP authentication traffic • Layer 2 messages on the D channel protocol errors and statistics Layer 2 messages on the B channel 29. When PPP authentication is enabled, which of the following may be checked before establishing a PPP link between two devices? (Choose two.) the enable password on the remote device the ip host configuration on the remote device • the security server database for the username and password of the remote device the hostname and enable password on the local device • the local database for the username and password of the remote device 30. How many separate B channel circuits can be provisioned on a PRI interface that uses a T1 line for connectivity? 2 16 • 23 24 30 128 31. Which operating systems support multiuser capability? (Choose three.) • Linux Windows 98 Windows ME • Windows XP • Windows 2000 32. What is placed in the address field of a frame that will travel from the DC office of ABC company to the Orlando office? MAC address of the Orlando router MAC address of the DC router 192.168.1.25 192.168.1.26 DLCI 100 • DLCI 200 33. What does a DLCI of 0 indicate about a frame? (Choose two.) This is the first data frame sent by the router. • This is a management frame. The encapsulation type is Cisco. The encapsulation type is IETF. • The LMI type is Ansi or q933a. The LMI type is Cisco. 34. Which of the following protocols can be used to encapsulate data traffic sent from a router BRI interface? (Choose two.) Link Access Protocol - Data • High-Level Data Link Control Logical Link Control Serial Data Link Control • Point to Point protocol Binary Synchronous Control protocol 35. An administrator consoled into the Jelly router needs to telnet to the Butter router. What DLCI will the Jelly router place in the frame to perform this operation? 110 115 220 • 225 36. Which commands can be used to identify which DLCIs are active? (Choose two.) • show frame-relay map show frame-relay lmi • show frame-relay pvc show frame-relay interface show interfaces show ip route 37. A technician is testing the functionality of a recently installed router. The technician is unable to ping the serial interface of a remote router. The technician executes the show interface serial0/0 command on the local router and sees the following line in the output: Serial0/0 is up, line protocol is down What are possible causes for this command output? (Choose three.) • remote CSU/DSU failure serial cable missing interface shutdown • keepalives not being sent • clocking signal missing 38. A router needs to forward a message received from a host. How does the router identify the correct VC to forward the message? (Choose two.) The router forwards the frame to all ports in the network and learns the address from the reply frame. The destination host IP address is embedded in the DLCI. • The router searches Inverse ARP tables for maps of DLCIs to IP addresses. • A table of static mappings can be searched. The router broadcasts a request for the required IP address. 39. Which of the following statements regarding point-to-point subinterfaces are true? (Choose two.) A point-to-point subinterface on one router must be connected to a similar subinterface on a remote router. Each point-to-point subinterface connection is configured with its own subnet. The DLCIs configured on the remote and local routers must be the same for the PVC. LMI frames are not transmitted through a subinterface. Routing updates in point-to-point networks are not subject to the split-horizon rule. 40. Which of the following can be concluded from the router output displayed in the graphic? (Choose two.) • The local DLCI number of this PVC is 100. The interface has been configured for subinterfaces and this map is for subinterface 0. • Inverse ARP has determined the remote ip address as 10.140.1.1. The LMI type is ANSI (0x64). There is currently no congestion on the link. 41. Which of the following are functions of the Local Management Interface used in Frame Relay networks? (Choose three.) • exchange information about the status of virtual circuits map DLCIs to network addresses • provide flow control provide error notification provide congestion notification • send keepalive packets to verify operation of the PVC 42. Which of the following describe functions of the Point-to-Point protocol with regards to the OSI model? (Choose three.) PPP uses Layer 3 of the OSI model to establish and maintain a session between devices. PPP operates at all layers of the OSI model. • PPP uses the data link layer to configure such options as error detection and compression. • PPP provides a mechanism to multiplex several network layer protocols. PPP uses Network Control Protocols (NCP) to test and maintain connectivity between devices. • PPP can be configured on both synchronous and asynchronous serial interfaces. 43. Which of the following describes the CHAP protocol? (Choose three.) • exchanges a random challenge number during the session to verfiy identity sends authentication password to verify identity • prevents transmission of login information in plain text • disconnects the PPP session if authentication fails initiates a two-way handshake 44. Which of the following switching types will allow the communication devices in the provider's network to be shared and only allocated to an individual subscriber during data transfer? circuit-switched • packet-switched frame-switched dedicated-switched lines lease-switched 45. How does Frame Relay technology process frames that contain errors? (Choose two.) • Frame Relay services depend on the upper layer protocols to handle error recovery. It requires the receiving device to request that the sender retransmit erroneous frames. FECN, BECN, and DE bits are set in the frames to minimize errors. • The receiving device drops any frames that contain errors without notifying the sender. The frame relay switch notifies the sender that errors were detected. 46. Which of the following describes the WAN devices and cabling shown in the graphic? (Choose two.) A null-modem cable is used between RouterD and DeviceC for connectivity. A DB-25 or DB-9 serial cable is connected to interface S0/0 of RouterA. • DeviceB and DeviceC are DCE devices. • The same encoding scheme must be used by DeviceB and DeviceC. A synchronous serial connection exists between DeviceB and DeviceC. | |
| Posted: 12 Sep 2009 08:45 AM PDT 1  Refer to the exhibit. The network administrator needs to setup Switch1 for remote access from HostA. The show ip interface brief is issued on Router1 and the show interfaces trunk command is issued on the Switch1 to verify the current status. The administrator applies the additional configuration shown in the exhibit to Switch1. However, the telnet from HostA fails. What additional commands need to be applied to the switch? Switch(config)# interface vlan 1 Switch(config-if)# ip address 10.1.1.250 255.255.255.0 Switch(config-if)# no shutdown Switch(config-if)# ip default-gateway 10.1.10.254 Switch(config)# interface vlan 1 Switch(config-if)# ip address 10.1.50.250 255.255.255.0 Switch(config-if)# no shutdown Switch(config-if)# ip default-gateway 10.1.50.254 Switch(config)# interface vlan 10 Switch(config-if)# ip address 10.1.10.250 255.255.255.0 Switch(config-if)# no shutdown Switch(config-if)# ip default-gateway 10.1.10.254 ==> Switch(config)# interface vlan 10 Switch(config-if)# ip address 10.1.1.250 255.255.255.0 Switch(config-if)# no shutdown Switch(config-if)# ip default-gateway 10.1.10.254 Switch(config)# interface vlan 50 Switch(config-if)# ip address 10.1.10.250 255.255.255.0 Switch(config-if)# no shutdown Switch(config-if)# ip default-gateway 10.1.10.254 2  Refer to the exhibit. On the basis of the configuration shown, how will an Ethernet frame on port GigabitEthernet0/1 be modified? 802.1Q encapsulation prepends a 4-byte tag field in front of the original Ethernet frame and recomputes the frame check sequence (FCS) on the modified frame. ==> 802.1Q encapsulation inserts a 4-byte tag field into the original Ethernet frame between the source address and type/length fields and recomputes the frame check sequence (FCS) on the modified frame. 802.1Q encapsulation prepends an 802.1p field in front of the original Ethernet frame and recomputes the frame check sequence (FCS) on the modified frame. 802.1Q encapsulation inserts an 802.1p field into the original Ethernet frame between the source address and type/length fields and recomputes the frame check sequence (FCS) on the modified frame. 3 What VLANs are allowed across a trunk when the range of allowed VLANs is set to the default value? ==> All VLANs will be allowed across the trunk. Only VLAN 1 will be allowed across the trunk. Only the native VLAN will be allowed across the trunk. The switches will negotiate via VTP which VLANs to allow across the trunk. 4 Which parameter is used to uniquely identify one wireless network from another? ==> SSID OFDM WEP DSSS 5  Refer to the exhibit. What is the consequence if SW1 port F0/1 is configured as an edge port? SW1 port F0/1 transitions to the learning state. ==> SW1 port F0/1 can generate a temporary loop. SW1 port F0/1 becomes a non-designated port. SW1 port F0/2 no longer passes BPDUs to SW4. 6  Refer to the exhibit. What will allow a host on VLAN 40 on switch X to communicate with a host in VLAN 40 on switch Y? QoS routing ==> trunking VPN 7  Refer to the exhibit. Spanning-tree port priorities are 128 for all interfaces. The network administrator enters the spanning-tree vlan 1 root primary command on S4. Which two port results are correct? (Choose two.) ==> S1 Gi0/1 becomes a root port. S2 Gi0/2 becomes a non-designated port. S3 Gi0/1 becomes a non-designated port. S4 Gi0/1 becomes a root port. ==> S4 Gi0/2 becomes a designated port. 8  Refer to the exhibit. Which two facts can be confirmed by this output? (Choose two.) This switch shows no configuration revision errors. This switch has established two-way communication with the neighboring devices. ==> This switch is configured to advertise its VLAN configuration to other VTP-enabled switches in the same VTP domain. This switch will drop all VTP advertisements that come from the switches that are configured in the same VTP domain. ==> This switch will cause no disruption in the VTP domain operations if the rest of the switches in the same VTP domain have a higher configuration revision number. 9  Refer to the exhibit. R1 is configured for traditional inter-VLAN routing. R1 can ping computer 3 but cannot ping computer 1. What is a possible cause for this failure? ==> S1 port Fa0/11 is in the wrong VLAN. R1 does not have an active routing protocol. The IP address of computer 1 is in the wrong logical network. Router interface Fa0/0 has the wrong trunk encapsulation type configured. 10  Refer to the exhibit. Both switches are interconnected via a trunk link. Host A and host B are on the default VLAN but are not able to exchange traffic. What should be done to fix the problem? Allow all VLANs on the trunk link. Remove the native VLAN from the trunk. Include a router or switch with Layer 3 capabilities. ==> Configure the same native VLAN on both ends of the trunk. 11  Refer to the exhibit. The hosts connected to switch SW1 are not able to communicate with the hosts in the same VLANs connected to switch SW2. What should be done to fix the problem? Configure VLANs with different VLAN IDs on switch SW2. ==> Reconfigure the trunk port on switch SW2 with static trunk configuration. Introduce a Layer 3 device or a switch with Layer 3 capability in the topology. Apply IP addresses that are in the same subnet to the interfaces used to connect SW1 and SW2. 12 What happens when the crypto key zeroize rsa command is entered on a switch configured with the transport input ssh command on the vty lines? A new RSA key pair is created. The switch defaults to allowing Telnet connections only. The switch is no longer able to make SSH connections as an SSH client. ==> The switch allows remote connections only after a new RSA key pair is generated. 13  Refer to the exhibit. An Ethernet switch has developed the CAM table shown. What action will the switch take when it receives the frame shown at the bottom of the exhibit? ==> forward the frame out all interfaces except Interface3 add station 00-00-3D-1F-11-05 to Interface2 in the forwarding table forward the frame out Interface3 discard the frame forward the frame out all interfaces forward the frame out Interface2 14 Which two statements describe Spanning Tree Protocol? (Choose two.) ==> It eliminates Layer 2 loops in network topologies. It eliminates the need for redundant physical paths in network topologies. ==> It can only be used in networks in which Layer 2 switching is in use. It can only be used in networks where both routers and switches are used together. It can only be used in networks where routers are installed. 15  Refer to the exhibit. A new host needs to be connected to VLAN 1. Which IP addresses should be assigned to this new host? 192.168.1.11 /28 ==> 192.168.1.22 /28 192.168.1.33 /28 192.168.1.44 /28 192.168.1.55 /28 16  Refer to the exhibit. How does SW1 manage traffic coming from Host A? SW1 drops the traffic because it is untagged. ==> SW1 leaves the traffic untagged and forwards it over the trunk. SW1 tags the traffic with the lowest VLAN ID value and forwards it over the trunk link. SW1 encapsulates the traffic with 802.1Q encapsulation and forwards it over the trunk link. 17 Refer to the exhibit. The switches are configured for VTP as shown. Which two statements correctly describe the operation of these switches? (Choose two.) A new VLAN can be added to Switch1 and that information will be added only to Switch2. ==> A new VLAN can be added to Switch1 and that information will be added to Switch2 and Switch4 ==> An existing VLAN can be deleted from Switch4 and that VLAN will be deleted from Switch1 and Switch2 An existing VLAN can be deleted from Switch2 and that VLAN will be deleted from Switch1 and Switch4. A new VLAN can be added to Switch4 and that information will be added to Switch1, Switch2, and Switch3. A new VLAN can be added to Switch3 and that information will be added to Switch1, Switch2, and Switch4. 18  Refer to the exhibit. Computer A sends a broadcast message. Which devices will see the broadcast? computer B computer B and Router1 ==> computer C and Router1 computer B, computer D, computer E and Router1 computer B, computer C, computer D, computer E and Router1 computer A, computer B, computer C, computer D, computer E and Router1 19  Refer to the exhibit. The network administrator enters the configuration shown to allow both SSH and Telnet connections to the switch. The Telnet connections fail. What is the most likely cause of this problem? The SSH version number is wrong. SSH has been configured on the wrong line. Telnet and SSH cannot be configured simultaneously. ==> The transport input command is configured incorrectly. 20  Refer to the exhibit. Which switch will be elected as the root bridge of the spanning tree topology? Cat-A Cat-B ==> Cat-C Cat-D 21  Refer to the exhibit. The switches in the exhibit have VTP pruning enabled. Which VLANs will be pruned from switch SW3? ==> VLAN 10 and VLAN 20 VLAN 1, VLAN 10, and VLAN 20 VLAN 1, VLAN 1002 through 1005 VLAN 1, VLAN 10, VLAN 20, VLAN 1002 through 1005 22  Refer to the exhibit. What does STATIC indicate in the output that is shown? The switch will not allow any other device to connect to port Fa0/15. ==> Traffic destined for MAC address 0000.c123.5432 will be forwarded to Fa0/15. This entry will be removed and refreshed every 300 seconds to keep it in the table. The switch learned this MAC address from the source address in a frame received on Fa0/15. When processing a frame, the switch does not have to perform a lookup to determine the final destination port. 23 Which three statements are true regarding router-on-a-stick inter-VLAN routing? (Choose three.) ==> requires the use of subinterfaces on the router requires an access link between the router and Layer 2 switch ==> more cost-efficient and scalable than using multiple physical interfaces requires each subinterface to be configured with the no shutdown command ==> can impact performance if many VLANs compete for bandwidth on a single router interface makes troubleshooting the inter-VLAN routing configuration much less complex than when using multiple physical interfaces 24  Refer to the exhibit. Router RA receives a packet with a source address of 192.168.1.35 and a destination address of 192.168.1.85. What will the router do with this packet? The router will forward the packet out interface FastEthernet 0/1.1. The router will forward the packet out interface FastEthernet 0/1.2. The router will forward the packet out interface FastEthernet 0/1.3. The router will forward the packet out interface FastEthernet 0/1.2 and interface FastEthernet 0/1.3. ==> The router will ignore the packet because the source and destination are on the same broadcast domain. The router will drop the packet since no network that includes the source address is attached to the router. 25  Refer to the exhibit. The network administrator needs to remove the east-hosts VLAN and use the switch port from that VLAN in one of the existing VLANs. What two commands should be used when completely removing VLAN 2 from S1-Central while leaving the switch and all its interfaces operational? (Choose two.) S1-Central# reload S1-Central# erase flash: ==> S1-Central(config)# no vlan 2 S1-Central# delete flash:vlan.dat ==> S1-Central(config-if)# switchport access vlan 3 26  Refer to the exhibit. What does "FORWARDING" mean in the command output shown? ==> The switch is sending and receiving data frames The switch is receiving BPDUs, but not sending data frames. The switch is participating in an election process by forwarding the BPDUs it receives. The switch is receiving BPDUs and populating the MAC address table, but not sending data. 27  Refer to the exhibit. Switch SW2 has been newly purchased and added to the network. What configuration should be applied to SW2 so that it participates in the same VTP domain as switch SW1, receives VLAN information from SW1, and synchronizes VLAN information? Disable VTP pruning on SW2. Configure SW2 in VTP transparent mode. ==> Configure SW2 with the VTP domain password. Configure SW2 as a VTP server with a higher revision number. 28 What are three benefits of a hierarchical network model? (Choose three.) ==> reduced contention for bandwidth reduced size of the physical layout ==> increased fault tolerance of the network elimination of the need for wiring closets elimination of the need for layer three functionality ==> simplification of management and troubleshooting 29  Refer to the exhibit. Which three options correctly identify information that could be associated with this output?(Choose three.) ==> Interface FastEthernet3/0/0 is subinterfaced. ==> A non-proprietary trunking protocol is in use. ==> The configuration is appropriate for a router-on-a-stick network design. A shutdown command has been applied to interface FastEthernet3/0/0. Interface FastEthernet3/0/0.3 is mapped to the default management VLAN. An IP address should be applied to FastEthernet3/0/0 for correct data routing. 30  Refer to the exhibit. Switch SW2 was tested in a lab environment and then inserted into a production network without reloading its configuration. After the trunk link between SW1 and SW2 was brought up, all users lost connectivity to the network. What could be the source of the problem? All the VLANs were pruned from the trunk port between SW1 and SW2. SW1 and SW2 cannot be both set as VTP servers in the same VTP domain. ==> VTP configuration revision number of SW2 was higher than the configuration revision number of SW1. The additional VLANs from SW2 created more VLANs than the VLAN database of SW1 could contain. 31  Refer to the exhibit. A network administrator needs to implement inter-VLAN routing on a hierarchical network. On which devices should the inter-VLAN routing be configured? AS1 and AS2 DS1 and DS2 ==> Gateway and CS1 Gateway, CS1, DS1, and DS2 32 Which three statements are correct concerning the default configuration of a new switch? (Choose three.) Spanning Tree Protocol is disabled. Enable password is configured as cisco. ==> All switch ports are assigned to VLAN1. ==> The flash directory contains the IOS image. VLAN1 is configured with a management IP address. ==> All interfaces are set to auto-negotiation of speed and duplex. 33  Refer to the exhibit. All hosts are in listen mode. Host 1 and Host 4 both transmit data at the same time. How do the hosts respond on the network? (Choose two.) ==> After the end of the jam signal, a backoff algorithm is invoked. Hosts 1 and 4 are operating full duplex so no collision will exist. The hub will block the port connected to Host 4 to prevent a collision. Hosts 1 and 4 are assigned shorter backoff values to provide them priority to access the media. ==> If a host has data to transmit after the backoff period of that host, the host checks to determine if the line is idle before transmitting. 34  Refer to the exhibit. After the listed commands are entered into router R1 and switch S1, the administrator enters the show interface fa0/1 trunk and gets the results shown. What is the likely problem? The trunk is established, but no VLANs have been configured to use it. ==> The trunk has not been established because the router does not support dynamic trunking protocol. The router, the switch, or both must be configured with the dynamic desirable option for dynamic trunking protocol to establish a trunk. The router is missing the dynamic trunking protocol statements necessary to form a trunk. 35  Refer to the exhibit. Which two statements are true about the operation of the interfaces? (Choose two.) Incoming traffic with VLAN ID 0 is processed by interface fa0/0. ==> Incoming traffic that has a VLAN ID of 2 is processed by subinterface fa0/0.2. Both subinterfaces remain up with line protocol up, even if fa0/0 line protocol is down. Subinterfaces use unique MAC addresses by adding the 802.1Q VLAN ID to the hardware address. ==> Traffic inbound on this router is processed by different subinterfaces, depending on the VLAN from which the traffic originated. 36 What three tasks should be performed before moving a Catalyst switch to another VTP management domain? (Choose three.) ==> Select the correct VTP mode and version. ==> Configure the switch with the name of the new management domain Download the VTP database from the VTP server in the new domain. Configure the VTP server in the new domain to recognize the BID of the switch. Reset the VTP counters to allow the switch to synchronize with the other switches in the new domain. ==> Verify that the switch has a lower configuration revision number than the other switches in the new domain 37  Refer to the exhibit. Hosts A and B, connected to hub HB1, attempt to transmit a frame at the same time but a collision occurs. Which hosts will receive the collision jamming signal? only hosts A and B ==> only hosts A, B, and C only hosts A, B, C, and D only hosts A, B, C, and E 38 Which statement regarding the service password-encryption command is true? The service password-encryption command is entered at the privileged EXEC mode prompt. The service password-encryption command encrypts only passwords for the console and VTY ports. ==> The service password-encryption command encrypts all previously unencrypted passwords in the running configuration. To see the passwords encrypted by the service password-encryption command, enter the no service password-encryption command. 39  Refer to the exhibit. Which two statements are true regarding what the cost value of 23 represents for Switch4? (Choose two.) ==> This cost represents the lowest cost path for Switch4 to the root switch. A cost of 23 is the value being advertised out port 16 on the switch upstream (closer) to the root switch. ==> Switch4 adds the cost of a Fast Ethernet link to 23 to determine its total cost to reach the root switch Switch4 is connected via a Fast Ethernet link to an upstream switch that in turn is directly connected to the root switch via a Gigabit Ethernet link. The root switch is advertising a cost of 23, which is lower than any other switch in the VLAN0001 spanning-tree domain. 40  Refer to the exhibit. What three statements describe why Host1 and Host2 are unable to communicate? (Choose three.) ==> The switch ports are on different VLANs. The switch IP address is on the wrong subnet. ==> The hosts are configured on different logical networks. ==> A router is required to forward traffic between Host1 and Host2. The VLAN port assignments must be contiguous for each VLAN. The host default gateway addresses must be on the same logical network. 41  Refer to the exhibit. Each switch is shown with its MAC address. Which switch will be elected as the spanning-tree root bridge if the switches are configured with their default priority values? switch A switch B switch C switch D switch E ==> switch F 42  Refer to the exhibit. Hosts PC_A and PC_B send traffic simultaneously, and the frames from the transmitting stations collide. What is the last device to receive the collision? hub HB1 ==> switch SW1 router R1 switch SW2 router R2 switch SW4 43 Why is it important that the network administrator consider the spanning-tree network diameter when choosing the root bridge? The network diameter limitation is 9. ==> BPDUs may be discarded because of expiring timers. The cabling distance between the switches is 100 meters. The network diameter must be set to the number of meters of the cable between the root bridge and its farthest connected switch. 44  Refer to the exhibit. A network administrator has segmented the network into two VLANs and configured Router1 for inter-VLAN routing. A test of the network, however, shows that hosts on each VLAN can only access local resources and not resources on the other VLAN. What is the most likely cause of this problem? ==> Switch port Fa0/1 is not trunking. Router interface Fa0/0 is possibly down. No routing protocol is configured on Router1. One of the router subinterfaces is possibly down. 45 What is the purpose of issuing the command switchport mode access on a switch interface? disable port security make the port operational override the default port behavior ==> force the port to be a part of a single vlan 46  Refer to the exhibit. Which statement is true regarding the information shown? Only one VLAN is currently configured to use the trunk links. The switch negotiated trunk links for interfaces Fa0/1 and Gi0/1. A Cisco proprietary protocol is in use for interfaces Fa0/1 and Gi0/1. ==> Interfaces Gi0/1 and Fa0/1 are allowed to carry data from multiple VLANs 47 Which identifier is used to keep track of frames that are destined for a particular wireless client? AID SSID ==> BSSID ESSID 48  Refer to the exhibit. What will happen when frames that contain an unknown source address reach interface fa0/24? A syslog message will be logged. Fa0/24 will become error-disabled. ==> The incoming frames will be dropped The security violation count will be incremented. 49 In which mode is a VTP switch operating if it has been configured to only forward VTP advertisements? client root server ==> transparent 50 Which method establishes an administrative connection for configuring the Linksys WRT300N wireless access point? Associate with the access point and then open a HyperTerminal session with the access point. Physically connect to the access point and then reboot the computer to launch the configuration software. ==> From a computer in the same IP subnet as the access point, enter the default IP address of the access point in a web browser. Modify the TCP/IP properties of the computer connected to the access point so that it exists on the same network, and then reboot your computer to establish a connection. 51 What two methods can be used to remove MAC address table entries from a switch? (Choose two.) The clear switching-tables command will remove statically configured entries. ==> The clear mac-address-table command will remove statically and dynamically configured table entries. The erase flash command will clear all statically configured table entries. Statically configured MAC addresses will automatically be removed from the address table 300 minutes after the last activity on a switch port. 52 What are two benefits of the IEEE 802.11n standard over the IEEE 802.11G? (Choose two.) requires less equipment ==> provides improved range ==> permits increased data rates has a single-input and a single-output needs no hardware upgrade for compatibility | |
| BitDefender Total Security 2010 – Proactive Protection Against Viruses, Spyware, Hackers, Spam Posted: 11 Sep 2009 10:35 PM PDT BitDefender Total Security application was designed to provide comprehensive proactive protection against viruses, spyware, hackers, spam and other Internet security threats, along with system maintenance and data backup. Here are some key features of "BitDefender Total Security": Confidently download, share and open files from friends, family, co-workers – and even total strangers: · Protects against viruses and other malware using industry-leading technology NEW · Scans all Web, e-mail and instant messaging traffic in real-time · Provides an unmatched detection rate of new threats based on two different proactive technologies · Blocks spyware programs that track your online activities Protect your identity: shop, bank, listen and watch, privately and securely: · Blocks web pages that attempt to steal your credit card data · Prevents personal information from leaking via e-mail, Web or instant messagingNEW · File Shredder permanently erases sensitive files and traces of files Guard your files and conversations with top-of-the line encryption: · Instant Messaging Encryption keeps your conversations private on Yahoo! and MSN Messenger · File Vault securely stores personal information or sensitive files · Automatically backs up files and folders · Connect securely to any network at home, at the office, or away: · The two-way firewall automatically secures your Internet connection wherever you are · Wi-Fi monitor helps prevent unauthorized access to your Wi-Fi network Protect your family and their computers: · Parental Control blocks access to inappropriate websites and e-mail · Limits kids' access the Internet, games, etc. to specific times · Makes it easy for you to manage the security of your network from a single location Play safely, play seamlessly: · Reduces the system load and avoids requesting user interaction during game play Get fine-tuned performance from your computer: · Removes unnecessary files & registry entries, for improved performance · Optimized scanning technology skips safe files for better scan speed and lower system load · Antispam stops unwanted e-mail from reaching your Inbox · Laptop Mode prolongs battery life Let professionals solve any security issues: · Assistance with common issues built directly into the product · Free technical support for the entire duration of the product license Requirements: · Available free hard disk space: 600 MB free space · Intel CORE Duo (1.66 GHz) or equivalent processor · RAM: · 1GB (Windows XP and Windows 7) · 1.5 GB (Windows Vista) · 600 MB available hard disk space · Internet Explorer 7 Limitations: · 30 days trial | |
| Posted: 11 Sep 2009 03:41 AM PDT Here you will find answers to SIMULATION Questions Question: A network associate is configuring a router for the weaver company to provide internet access. The ISP has provided the company six public IP addresses of 198.18.184.105 198.18.184.110. The company has 14 hosts that need to access the internet simultaneously. The hosts in the company LAN have been assigned private space addresses in the range of 192.168.100.17 – 192.168.100.30.
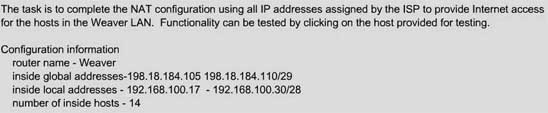 Solution: The company has 14 hosts that need to access the internet simultaneously but we just have 6 public IP addresses from 198.18.184.105 to 198.18.184.110/29. Therefore we have to use NAT overload (or PAT) Double click on the Weaver router to open it Router>enable Router#configure terminal First you should change the router's name to Weaver Router(config)#hostname Weaver Create a NAT pool of global addresses to be allocated with their netmask.Weaver(config)#ip nat pool mypool 198.18.184.105 198.18.184.110 netmask 255.255.255.248 Create a standard access control list that permits the addresses that are to be translatedWeaver(config)#access-list 1 permit 192.168.100.16 0.0.0.15 Establish dynamic source translation, specifying the access list that was defined in the prior step Weaver(config)#ip nat inside source list 1 pool mypool overload This command translates all source addresses that pass access list 1, which means a source address from 192.168.100.17 to 192.168.100.30, into an address from the pool named mypool (the pool contains addresses from 198.18.184.105 to 198.18.184.110) Overload keyword allows to map multiple IP addresses to a single registered IP address (many-to-one) by using different ports The question said that appropriate interfaces have been configured for NAT inside and NAT outside statements. This is how to configure the NAT inside and NAT outside, just for your understanding: Weaver(config)#interface fa0/0 Weaver(config-if)#ip nat inside Weaver(config-if)#exit Weaver(config)#interface s0/0 Weaver(config-if)#ip nat outside Weaver(config-if)
|














0 comments:
Post a Comment