Avaya preps one-box data-center strategy |
- Avaya preps one-box data-center strategy
- German regulators welcome street panorama privacy law draft
- IIA pushes new ISP spam code
- Google moves encrypted search to a new site
- Using TCP Intercept to mitigate DoS SYN Attacks
- FTC says scammers stole millions, using virtual companies
| Avaya preps one-box data-center strategy Posted: 28 Jun 2010 09:00 AM PDT |
| German regulators welcome street panorama privacy law draft Posted: 28 Jun 2010 09:00 AM PDT |
| Posted: 28 Jun 2010 09:00 AM PDT |
| Google moves encrypted search to a new site Posted: 28 Jun 2010 09:00 AM PDT |
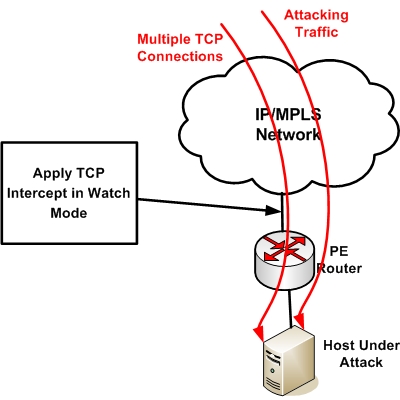
| Using TCP Intercept to mitigate DoS SYN Attacks Posted: 28 Jun 2010 02:27 AM PDT The most common attack against Service Provider IP Networks is Denial of Service. Usually these attacks take the form of "Many-to-One Attacks" where multiple attacking sources send flooding traffic towards a single destination. These attacks are sometimes called Distributed Denial of Service. Usually the attacking hosts are "zombie" computers which are compromised by hackers and belong to a BotNet network. Usually these attacks are directed towards a critical node of the ISP network (a Border Router, a public Server etc). If the attack contains thousands of non-legitimate connections to initiate TCP communication (SYN packets) towards a single host, the target host gets overloaded from the requested connections because the three-way TCP handshake does not get completed (because these TCP connections have unreachable return addresses, the connections cannot be established). The resulting volume of unresolved open connections eventually overwhelms the server and can cause it to deny service to valid requests. The above attack is also called SYN Attack.
TCP Intercept is a feature on routers used to prevent and mitigate TCP SYN-flooding attacks by monitoring the rate of SYN packets and intervening inside the TCP communication whenever necessary in order to reduce the number of incomplete TCP connections. There are two modes for TCP Intercept: "Intercept Mode" and "Watch Mode". Intercept Mode The most "invasive" mode is "Intercept Mode". The router establishes a connection with the client on behalf of the destination server, and if successful, establishes the connection with the server on behalf of the client and knits the two half-connections together transparently. This means that if the connection is legitimate, it will reach the server with no problem. If the connection is from a non-legitimate client, the half-open connection will be dropped by the router. This mode consumes a lot of memory and CPU on the router. Watch Mode We recommend using the "Watch Mode" instead of the "Intercept Mode". In Watch Mode, the router passively watches the connection requests flowing through the router. If a connection fails to get established in a configurable interval, the software intervenes and terminates the connection attempt. Configuration of TCP Intercept On router connecting the host under attack, configure the following (assume target host under attack is 1.1.1.1): Router(config)# access-list 101 permit tcp any host 1.1.1.1 The above configuration will watch the TCP SYN packets towards host 1.1.1.1. If the SYN packets exceed a certain default value, the router starts to close incomplete TCP connections. Specifically, if the number of incomplete connections exceed 1,100, or the number of connections arriving in the last one-minute period exceed 1,100, each new arriving connection causes the oldest partial connection (or a random connection) to be deleted. These are the default values, which can be altered. |
| FTC says scammers stole millions, using virtual companies Posted: 28 Jun 2010 09:00 AM PDT |
| You are subscribed to email updates from "Cisco" via ehsan in Google Reader To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google Inc., 20 West Kinzie, Chicago IL USA 60610 | |












0 comments:
Post a Comment