GPUs: Powering Your Gaming and Cracking Your Passwords |
- GPUs: Powering Your Gaming and Cracking Your Passwords
- NSS Labs: Testing shows most AV suites fail against exploits
- HP to buy vulnerability specialist Fortify Software
- DOJ won't file charges in school webcam spying case
- How to Spot Facebook Scams Like 'Dislike'
- Facebook popularity eats company bandwidth
- Beware the Facebook "Dislike" Button Scam
- Malicious widget hacked millions of Web sites
- Auto finance company scopes GPS tracking
- Microsoft and Google fight over e-mail, but agree on $5 inboxes
- Five billionth device about to plug into Internet
- How to Configure Static Routing on Cisco Routers
| GPUs: Powering Your Gaming and Cracking Your Passwords Posted: 17 Aug 2010 09:00 AM PDT |
| NSS Labs: Testing shows most AV suites fail against exploits Posted: 17 Aug 2010 09:00 AM PDT |
| HP to buy vulnerability specialist Fortify Software Posted: 17 Aug 2010 09:00 AM PDT |
| DOJ won't file charges in school webcam spying case Posted: 17 Aug 2010 09:00 AM PDT |
| How to Spot Facebook Scams Like 'Dislike' Posted: 17 Aug 2010 09:00 AM PDT |
| Facebook popularity eats company bandwidth Posted: 17 Aug 2010 09:00 AM PDT |
| Beware the Facebook "Dislike" Button Scam Posted: 16 Aug 2010 09:00 AM PDT Facebook recently expanded the "Like" feature, allowing users of the social networking site to "like" individual comments to a given post, and expanding the application of the voting system to other sites. Now, a malware scam is circulating that exploits the demand from Facebook users for its antithesis--the "Dislike" button. |
| Malicious widget hacked millions of Web sites Posted: 16 Aug 2010 09:00 AM PDT |
| Auto finance company scopes GPS tracking Posted: 16 Aug 2010 09:00 AM PDT |
| Microsoft and Google fight over e-mail, but agree on $5 inboxes Posted: 16 Aug 2010 09:00 AM PDT |
| Five billionth device about to plug into Internet Posted: 16 Aug 2010 09:00 AM PDT |
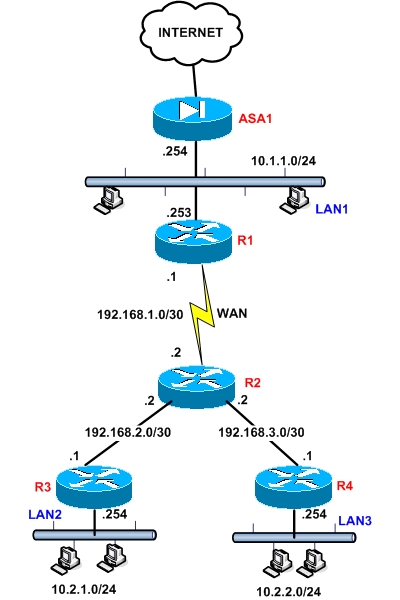
| How to Configure Static Routing on Cisco Routers Posted: 17 Aug 2010 01:41 AM PDT Cisco IOS Routers support both static and dynamic routes. In small networks (2 to 5 routers) I would suggest to configure only static routes, especially if the network is not going to change much over time. Of course dynamic routing (using dynamic routing protocols such as RIP, OSPF, EIGRP) is much more flexible and scalable (for larger networks) but gets a little bit tricky to troubleshoot in case of problems. There is also the option to mix static and dynamic routing if needed, but you need to take into consideration issues such as route redistribution (you will usually need to redistribute static routes into the dynamic protocol). In this post I will try to illustrate static routing using a small network scenario (see picture below) and explain also some other issues related with ICMP Redirects and Cisco ASA firewall.
Network Description From the example network above, we have a Cisco ASA firewall (ASA1) protecting our internal networks from the Internet. LAN1 is a Class C network subnet (10.1.1.0/24) which has user computers connected (this might be the headquarters LAN of the Enterprise). There is also a Router (R1) serving as a WAN router to connect a distant remote office over a WAN link. At the other side of the WAN link we have R2 which serves as the Hub router having two spokes (R3, R4). There are also two more LAN networks with user computers (LAN2 connected to R3 and LAN3 connected to R4). The IP addresses assigned to the network are as following: ASA1 Internal IP: 10.1.1.254 R1 IP on LAN1 network: 10.1.1.253 R2 IP on the WAN link: 192.168.1.2 R3 IP connected with R2: 192.168.2.1 R4 IP connected with R2: 192.168.3.1 LAN1 network: 10.1.1.0/24 Traffic Flow Requirements We need to have the following communication between networks:
Configuration of Static Routing The intention of this article is to explain static routing only, so I will not get into the full configuration details of all devices in the network. I will just show snippets of commands for static routes. The general format of a static route command on a Cisco router is: Router(config)# ip route [destination network] [mask] [gateway address] The command above tells the router the following information: "if you want to send a packet to the following "destination network", then send it to this "gateway address". The format of a static route command on a Cisco ASA firewall is: ASA(config)# route [interface name] [destination network] [mask] [gateway] Now let's see the commands needed for each router. It's more convenient to start from the bottom up: Router R3: R3(config)# ip route 0.0.0.0 0.0.0.0 192.168.2.2 We just need a default route on this router to send ALL traffic towards R2 gateway address (192.168.2.2). Router R4: R4(config)# ip route 0.0.0.0 0.0.0.0 192.168.3.2 Similar with R3, we just need a default route on this router to send ALL traffic towards R2 gateway address (192.168.3.2). Router R2: ! Default route ! Static routes to reach LAN2 and LAN3 This is a little tricky. We need both a default route (to send all upwards traffic, including traffic to the Internet, towards R1) and also we need two specific static routes to reach LAN2 and LAN3 network. The two specific static routes (two last lines) are needed for the reply packets from LAN2 and LAN3 and also for LAN1 to be able to reach LAN2/LAN3. Router R1: ! Default Route towards ASA for Internet Traffic ! Static routes to reach LAN2 and LAN3 ! Static routes to reach transit point-to-point networks Firewall ASA1: ASA1(config)# route outside 0.0.0.0 0.0.0.0 [asa gateway IP] ! Static routes to reach LAN2 and LAN3 The ASA will need a default route towards its default gateway IP (assigned by the ISP), and also two static routes to reach the distant LAN2 and LAN3 networks. You DO NOT need a static route for LAN1 network because it is directly connected to the ASA. Default Gateway for LAN1 computers As we said before, one of the traffic flow requirements was to access LAN2 and LAN3 networks from LAN1 computers. If I ask you what should be the default gateway address configured on LAN1 computers, most of you would answer "The ASA internal address 10.1.1.254". However, this is WRONG. Let me explain why. Assume you configure the default gateway address for LAN1 hosts to be the ASA address 10.1.1.254. If HostA on LAN1 wants to send traffic to the Internet, then it will send it to its default gateway address (ASA firewall) which will forward the packet to the Internet. So far so good. However, if HostA wants to send traffic to LAN2 or LAN3 hosts, it will again send the traffic to the ASA which is supposed to send an ICMP Redirect to HostA and tell him "hey, you should really be using 10.1.1.253 to get to LAN2 or LAN3". However, the Cisco ASA is NOT ABLE to send an ICMP Redirect like it should. Therefore, HostA will never be able to communicate with LAN2/LAN3. If the ASA was a router instead, everything would work fine because routers actually are able to send ICMP Redirects. So, the correct answer is to configure all hosts on LAN1 network to have Default Gateway address the IP of R1 (10.1.1.253). This way, they will be able to access both the Internet and the other internal LAN networks (LAN2/LAN3). For any questions or comments please fill out the comment form below. |
| You are subscribed to email updates from "Cisco" via ehsan in Google Reader To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google Inc., 20 West Kinzie, Chicago IL USA 60610 | |












0 comments:
Post a Comment