DsmbISP_Final_Exam_-_CCNA |
- DsmbISP_Final_Exam_-_CCNA
- ICO compares TalkTalk anti-malware technology to Phorm
- Enterprise risk management: Get started in six steps
- Return of the Spam Heckler
- ACLU, other groups sue US gov't over border laptop searches
- Microsoft investigates two-year-old IE bug
- Basic Cisco 800 Router Configuration for Internet Access
| Posted: 07 Sep 2010 06:05 PM PDT |
| ICO compares TalkTalk anti-malware technology to Phorm Posted: 07 Sep 2010 09:00 AM PDT |
| Enterprise risk management: Get started in six steps Posted: 07 Sep 2010 09:00 AM PDT |
| Posted: 07 Sep 2010 09:00 AM PDT About a year ago, I wrote an article for this site that began by praising the craft required to produce a spam header intriguing enough to coax an innocent recipient into opening the unsolicited message (see "Straight to the Spam Folder: Astonishing E-Mail Messages You'll Never Open"). Then I spent the rest of the story mocking various spam headers that editors at PCWorld had recently received. |
| ACLU, other groups sue US gov't over border laptop searches Posted: 07 Sep 2010 09:00 AM PDT |
| Microsoft investigates two-year-old IE bug Posted: 07 Sep 2010 09:00 AM PDT |
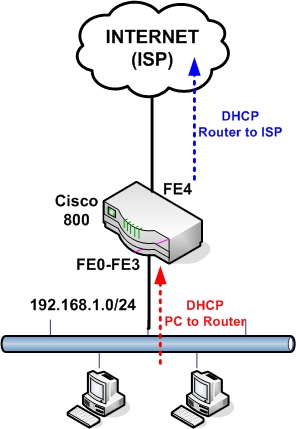
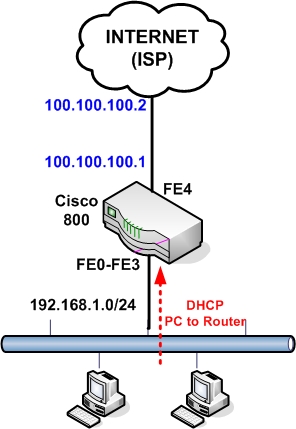
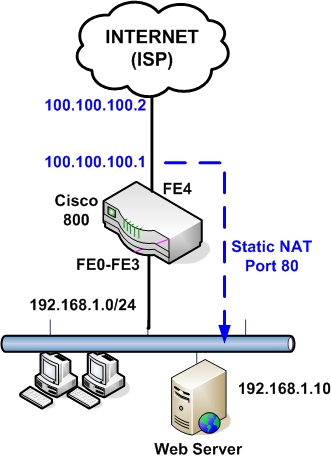
| Basic Cisco 800 Router Configuration for Internet Access Posted: 07 Sep 2010 01:13 AM PDT The Cisco 800 series routers are part of the "Branch Office" category, used mainly for SOHO purposes or for connecting remote branch offices to a central location. They are "fixed hardware configuration" devices, meaning that they don't have any plug-in hardware slots for inserting additional interfaces to the device (all the interfaces are fixed). All the 800 series models come with a 4-port 10/100 managed switch used for connecting the internal LAN computers, and with an IOS software that supports security features including the Firewall set. The main difference of each model is the WAN interface. All models that end with "1" in the model number (i.e 851, 861, 871, 881, 891) have a 10/100 Fast Ethernet interface as a WAN port. The other models have an xDSL type WAN port (i.e ADSL, G.SHDL, VDSL2). Also, all models have the option of a WiFi Radio interface (the model number ends with a "W", e.g 851W, 857W, 861W etc). In this post I will describe a basic configuration scenario for connecting a Cisco 800 router for Internet access. I will use a model with an Ethernet WAN interface (such as 851, 861, 871, etc) since those models are the most popular. Something to have in mind for all 800 series routers, the four LAN interfaces (FE0 up to FE3) are Layer2 switch interfaces that are assigned by default to Vlan1. This means that you can not assign an IP address directly to the LAN interfaces. The IP address for the LAN-facing side of the router is assigned under "interface Vlan1". On the other hand, the WAN interface (FE4) is a normal Layer3 router port, which means you can assign an IP address directly on the interface ("interface FastEthernet4"). I will describe three basic scenarios which are frequently encountered in real networks.
Scenario 1:
Configuration: The following is the basic configuration needed for the simple scenario above. configure terminal enable secret somesecretpassword ! Configure the DHCP pool to assign addresses to internal hosts ! Do not assign addresses 1 to 30 ! This is the LAN facing interface of the 800 router. Used as gateway for PCs ! Interfaces FE0 to FE3 are Layer 2 interfaces interface FastEthernet2 interface FastEthernet3 ! This is the WAN interface getting address via DHCP from the ISP ! Configure NAT. All internal hosts will be nated on the WAN interface ip route 0.0.0.0 0.0.0.0 fastethernet4 line vty 0 4 Scenario 2:
Configuration: This is the same configuration as scenario 1 except that the WAN IP address is static and also the default gateway of our ISP is known. The only difference from the configuration above is on the WAN interface and on default route: ! This is the WAN interface with static IP interface FastEthernet 4 ip route 0.0.0.0 0.0.0.0 100.100.100.2 Scenario 3:
Configuration: Here the WAN address is static and we have also an internal Web Server for which we need to allow HTTP access from Internet. To do this we must configure a static NAT with port redirection. Traffic that comes towards our WAN public address 100.100.100.1 on port 80 will be redirected by the router to the internal Web Server at address 192.168.1.10 on port 80. configure terminal enable secret somesecretpassword ! Configure the DHCP pool to assign addresses to internal hosts ! Do not assign addresses 1 to 30 ! This is the LAN facing interface of the 800 router. Used as gateway for PCs ! Interfaces FE0 to FE3 are Layer 2 interfaces interface FastEthernet1 interface FastEthernet2 interface FastEthernet3 ! This is the WAN interface with static IP ! Configure NAT. All internal hosts will be nated on the WAN interface ! Configure static NAT for port redirection ip route 0.0.0.0 0.0.0.0 100.100.100.2 line vty 0 4 |
| You are subscribed to email updates from "Cisco" via Ehsan in Google Reader To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google Inc., 20 West Kinzie, Chicago IL USA 60610 | |












0 comments:
Post a Comment