RIP Routing Fundamentals |
- RIP Routing Fundamentals
- The Cisco Three-Layered Hierarchical Model
- Facebook Quick Tip: Control Apps Access To Your Data
- Best practices for endpoint security, Part 2
- Facebook's new groups feature worries some
- Microsoft plans colossal Patch Tuesday next week
- Facebook takes on privacy with new tools
- Prepare for Record Onslaught of Patches from Microsoft
- Oracle, Microsoft ready major security updates
- Aldi data breach shows payment terminal holes
| Posted: 08 Oct 2010 04:40 PM PDT
1. Hop Count Limit: Destination that is more than 15 hops away is considered unreachable by RIPv1. 2. Classful Routing Only: RIP is a classful routing protocol. RIPv1 doesn't support classless routing. RIP v1 advertises all networks it knows as classful networks, so it is not possible to subnet a network using RIP v1. 3. Metric limitation: The best route in RIP is determined by counting the number of hops required to reach the destination. A lower hop count route is always preferred over a higher hop count route. One disadvantage of using hop count as metric is that if there is a route with one additional hop, but with significantly higher bandwidth, the route with smaller bandwidth is taken. This is illustrated in the figure below: 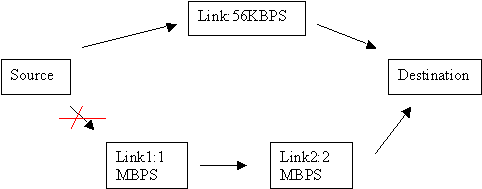 The RIP routed packets take the path through 56KBPS link since the destination can be reached in one hop. Though, the alternative provides a minimum bandwidth of 1MBPS (though using two links of 1MBPS, and 2MBPS each), it represents 2 hops and not preferred by the RIP protocol. Features of RIP v2:RIP v2 is a revised version of its predecessor RIP v1. The following are the important feature enhancements provided in RIPv2:1. RIPv2 packets carry the subnet mask in each route entry, making RIPv2 a classless routing protocol. It provides support for variable-length subnet masking (VLSM) and classless addressing (CIDR). 2. Next Hop Specification: In RIPv2, each RIP entry includes a space where an explicit IP address can be entered as the next hop router for datagrams intended for the network in that entry. For example, this field can be used when the most efficient route to a network is through a router that is not running RIP. Since, that a router will not exchange RIP messages, explicit Next Hop field allows the router to be selected as the next hop router. 3. Authentication: RIPv1 does not support authentication. This loophole may be used maliciously by hackers, that may resulting in delivering the data packets to a fictitious destination as determined by the hacker. RIPv2 provides a basic authentication scheme, so that a router can accept RIP messages from a neighboring router only after ascertaining its authenticity. 4. Route Tag: Each RIPv2 entry includes a Route Tag field, where additional information about a route can be stored. It provides a method for distinguishing between internal routes (learned by RIP) and external routes (learned from other protocols). Limitations of RIP v2:One of the biggest limitations of RIPv1 still remains with RIPv2. It is hop count limitation, and metric. The hop count of 16 still remains as unreachable, and the metric still remains hop count. A smaller hop count limits the network diameter, that is the number of routers that can participate in the RIP network.Example Question: While the packet travels from source to destination through an Internetwork, which of the following statements are true? (Choose 2 best answers). A. The source and destination hardware (interface) addresses change B. The source and destination hardware (interface) addresses remain constant. C. The source and destination IP addresses change D. The source and destination IP addresses remain constant. Ans. A, D Explanation: While a packet travels through an Internetwork, it usually involves multiple hops. It is important to know that the logical address (IP address) of the source (that created the packet) and destination (final intended destination) remain constant, whereas the hardware (interface) addresses change with each hop. | ||
| The Cisco Three-Layered Hierarchical Model Posted: 08 Oct 2010 04:44 PM PDT Cisco has defined a hierarchical model known as the hierarchical internetworking model. This model simplifies the task of building a reliable, scalable, and less expensive hierarchical internetwork because rather than focusing on packet construction, it focuses on the three functional areas, or layers, of your network: Core layer: This layer is considered the backbone of the network and includes the high-end switches and high-speed cables such as fiber cables. This layer of the network does not route traffic at the LAN. In addition, no packet manipulation is done by devices in this layer. Rather, this layer is concerned with speed and ensures reliable delivery of packets. Distribution layer: This layer includes LAN-based routers and layer 3 switches. This layer ensures that packets are properly routed between subnets and VLANs in your enterprise. This layer is also called the Workgroup layer. Access layer: This layer includes hubs and switches. This layer is also called the desktop layer because it focuses on connecting client nodes, such as workstations to the network. This layer ensures that packets are delivered to end user computers. Figure INT.2.1 displays the three layers of the Cisco hierarchical model. 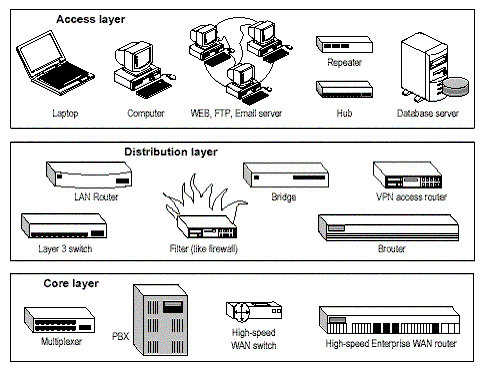 When you implement these layers, each layer might comprise more than two devices or a single device might function across multiple layers.The benefits of the Cisco hierarchical model include:
Core LayerThe core layer is responsible for fast and reliable transportation of data across a network. The core layer is often known as the backbone or foundation network because all other layers rely upon it. Its purpose is to reduce the latency time in the delivery of packets. The factors to be considered while designing devices to be used in the core layer are:
| ||
| Facebook Quick Tip: Control Apps Access To Your Data Posted: 08 Oct 2010 09:00 AM PDT | ||
| Best practices for endpoint security, Part 2 Posted: 08 Oct 2010 09:00 AM PDT To cyber thieves, endpoint devices are a tempting target. Such devices can be a treasure trove of sensitive information in their own right, but they are also the gateway to bigger targets like network servers, databases and applications. In this article, security experts Faycal Daira and Bob Foley offer even more of their best practices for endpoint protection. Last week we looked at antivirus, device control, and host-IPS and behavioral protections. This week we cover location awareness, network access control and application control. | ||
| Facebook's new groups feature worries some Posted: 08 Oct 2010 09:00 AM PDT | ||
| Microsoft plans colossal Patch Tuesday next week Posted: 07 Oct 2010 09:00 AM PDT | ||
| Facebook takes on privacy with new tools Posted: 07 Oct 2010 09:00 AM PDT | ||
| Prepare for Record Onslaught of Patches from Microsoft Posted: 07 Oct 2010 09:00 AM PDT | ||
| Oracle, Microsoft ready major security updates Posted: 07 Oct 2010 09:00 AM PDT | ||
| Aldi data breach shows payment terminal holes Posted: 07 Oct 2010 09:00 AM PDT | ||
| You are subscribed to email updates from "Cisco" via Ehsan in Google Reader To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google Inc., 20 West Kinzie, Chicago IL USA 60610 | |












0 comments:
Post a Comment