Russia detains suspect in carding, online fraud scheme |
- Russia detains suspect in carding, online fraud scheme
- Oracle to buy SSO vendor Passlogix
- Cloud computing in the U.S. shows momentum
- BT defers court case seeking downloader details
- Facebook users warned over 'free iPhone' scam
- PCI security group speaks out on encryption
- Facebook hit by new iPhone spam attack
- Symantec Unveils Strategy to Protect Mobile Devices and Data
- EU Parliamentarians move to block anti-counterfeiting pact
- Piracy group threatens more DDoS attacks
- Cisco bolsters branch switches, routers
- HP branches out
- Cisco expands 11n Wi-Fi line, mobile VPN client
- Cisco launches high-end security appliance
- Routing Fundamentals
- Start-up CloudFlare secures Web sites and improves loading times
- Why to Celebrate National Cyber Security Awareness Month
- Online groups introduce labeling for targeted ads
- Collaboration, training key to Westpac's security success
| Russia detains suspect in carding, online fraud scheme Posted: 05 Oct 2010 09:00 AM PDT | ||||||||||||||||||||
| Oracle to buy SSO vendor Passlogix Posted: 05 Oct 2010 09:00 AM PDT | ||||||||||||||||||||
| Cloud computing in the U.S. shows momentum Posted: 05 Oct 2010 09:00 AM PDT | ||||||||||||||||||||
| BT defers court case seeking downloader details Posted: 05 Oct 2010 09:00 AM PDT | ||||||||||||||||||||
| Facebook users warned over 'free iPhone' scam Posted: 05 Oct 2010 09:00 AM PDT | ||||||||||||||||||||
| PCI security group speaks out on encryption Posted: 05 Oct 2010 09:00 AM PDT | ||||||||||||||||||||
| Facebook hit by new iPhone spam attack Posted: 05 Oct 2010 09:00 AM PDT | ||||||||||||||||||||
| Symantec Unveils Strategy to Protect Mobile Devices and Data Posted: 05 Oct 2010 09:00 AM PDT Recognizing that the technology landscape is shifting rapidly toward mobility, Symantec today unveiled new tools to help protect mobile devices, and the sensitive data they contain. The mobile security and management strategy from Symantec enables businesses, service providers, and users to manage and secure mobile devices no matter where they may roam. | ||||||||||||||||||||
| EU Parliamentarians move to block anti-counterfeiting pact Posted: 05 Oct 2010 09:00 AM PDT | ||||||||||||||||||||
| Piracy group threatens more DDoS attacks Posted: 05 Oct 2010 09:00 AM PDT | ||||||||||||||||||||
| Cisco bolsters branch switches, routers Posted: 05 Oct 2010 04:59 AM PDT | ||||||||||||||||||||
| Posted: 05 Oct 2010 09:00 AM PDT HP unveiled new products and services across its networking, security and computing portfolios designed to improve application performance and delivery. Rival Cisco also announced its own branch office application acceleration extensions this week, and the two are expected to compete aggressively in this space with their respective new offerings. | ||||||||||||||||||||
| Cisco expands 11n Wi-Fi line, mobile VPN client Posted: 05 Oct 2010 09:00 AM PDT | ||||||||||||||||||||
| Cisco launches high-end security appliance Posted: 05 Oct 2010 09:00 AM PDT | ||||||||||||||||||||
| Posted: 05 Oct 2010 07:03 AM PDT
One often get confused between a routing protocol and a routed protocol. A routing protocol such as RIP is used to route information packets over the Internet, where as a routed protocol such as IP (or IPX) is the payload (contains data) that get routed from source to the destination. Routing protocols are primarily distinguished into three types:
The table below provides the routing protocol used with different routed protocols:
Routing Metric: This is a fundamental measure that routing protocols use for determining appropriate route to deliver packets. Each routing protocol uses its own measure of metric, and a sample of routing metrics used by different routing protocols is given below:
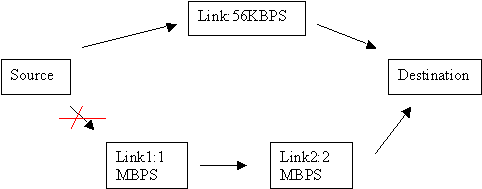 The RIP routed packets take the path through 56KBPS link since the destination can be reached in one hop. Though, the alternative provides a minimum bandwidth of 1MBPS (though using two links of 1MBPS, and 2MBPS each), it represents 2 hops and not preferred by the RIP protocol. Link State vs. Distance VectorDistance Vector routing protocols usually send their entire routing table to their nearest neighbors at regular intervals. A router that receives several such routing tables filter the routes and arrive at its own and retransmits it to its neighbouring routers. There will some period of time where different routers hold non-optimized routes initially. After some time, known as convergence time, a final routing table is arrived at by all the routers. A faster convergence time results in a stable network.RIP, as mentioned earlier uses hop count as the metric for computing a route to a given destination. Other Distance Vector routing protocols, such as IGRP, improve on this by using hop count, bandwidth, current load, cost, and reliability to determine the best path. Link State routing protocols usually send only the routing changes to every other router within their area. Unlike Distance Vector, routers using Link State routing protocols maintain a picture of the entire network. A router can use this network wide information to determine the best route for traffic. Example Question: What is true about IP routing? A. The frame changes at each hop B. The source IP address changes at each hop C. The destination IP address changes at each hop D. The hardware interface addresses remain constant Correct answer: A Explanation: IP Packets are transported from source network to the destination network by what is known as routing. Hop-by-hop routing model is used by the Internet for delivery of packets. At each hop, the destination IP address is examined, the best next hop is determined by the routing protocol (such as RIP, OSPF or BGP) and the packet is forwarded by one more hop through this route. The same process takes place at the next hop. During this process, the logical addresses remain same. In an IP network, the logical addresses are IP addresses. The hardware interface addresses, such as MAC address change with each hop. | ||||||||||||||||||||
| Start-up CloudFlare secures Web sites and improves loading times Posted: 04 Oct 2010 09:00 AM PDT | ||||||||||||||||||||
| Why to Celebrate National Cyber Security Awareness Month Posted: 04 Oct 2010 09:00 AM PDT It's that time of year again. The weather is turning cooler, football season has begun, Halloween is fast approaching. That can only mean one thing--it's National Cyber Security Awareness Month! Just in case you aren't really sure what the big deal is, or why you should care, here are five recent security threats that highlight why we need an entire month to raise awareness and promote better computer and network security. | ||||||||||||||||||||
| Online groups introduce labeling for targeted ads Posted: 04 Oct 2010 09:00 AM PDT | ||||||||||||||||||||
| Collaboration, training key to Westpac's security success Posted: 04 Oct 2010 09:00 AM PDT |
| You are subscribed to email updates from "Cisco" via Ehsan in Google Reader To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google Inc., 20 West Kinzie, Chicago IL USA 60610 | |












0 comments:
Post a Comment