Mozilla adds 'Do Not Track' to newest Firefox 4 beta |
- Mozilla adds 'Do Not Track' to newest Firefox 4 beta
- Google boosts log-in protection for its users
- Security startup hopes it holds key for cloud encryption
- RSA Conference 2011: Cloud security challenges dominate
- CCNA1 Final <= NEWS 2010
- IP Addressing
- CCNA 4 Chapter 8
- CCNA 4 Final Exam V4.0 2010
- Engineer,CCNA ATM VOIP Lan Wan
- All Answer CCNA1, CCNA2, CCNA3, CCNA4, CCNA Final
- Redistribution : Rip & OSPF Using Packet Tracer
- TCL Scripting in IOS. Easy to understand Tutorial !
- DsmbISP_Final_Exam_-_CCNA
- CCNA3 Final 2010
- Routing Fundamentals
- CCNA 1 Final Exam 2010
- CCNA4 Final Exam (French)
- Subnet masking
- CCNA Wireless - Any netsims available?
- Free CCNA Practice Test
| Mozilla adds 'Do Not Track' to newest Firefox 4 beta Posted: 10 Feb 2011 08:47 AM PST | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Google boosts log-in protection for its users Posted: 10 Feb 2011 07:56 AM PST | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Security startup hopes it holds key for cloud encryption Posted: 10 Feb 2011 07:17 AM PST | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| RSA Conference 2011: Cloud security challenges dominate Posted: 10 Feb 2011 06:17 AM PST | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Posted: 18 Nov 2010 05:16 PM PST
Contact me at: nguyenhuuhai.it@gmail.com | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Posted: 30 Sep 2010 06:18 AM PDT
Address ClassesThere are 5 different address classes. You can determine which class any IPaddress is in by examining the first 4 bits of the IP address.
Now we can see how the Class determines, by default, which part of the IP address belongs to the network (N) and which part belongs to the Host/node (H).
In order to specify the network address for a given IP address, the node section is set to all "0"s. In our example, 192.189.210.0 specifies the network address for 192.189.210.078. When the node section is set to all "1"s, it specifies a broadcast that is sent to all hosts on the network. 192.189.210.255 specifies the broadcast address. Private SubnetsThere are three IP network addresses reserved for private networks. The addresses are 10.0.0.0/8, 172.16.0.0/12, and 192.168.0.0/16. They can be used by anyone setting up internal IP networks, such as an intranet. Internet routers never forward the private addresses over the public Internet. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Posted: 26 Oct 2010 06:46 AM PDT 1. What combination of IP address and wildcard mask should be used to specify only the last 8 addresses in the subnet 192.168.3.32/28? 192.168.3.32 0.0.0.7 192.168.3.32 0.0.0.15 192.168.3.40 0.0.0.7 192.168.3.40 0.0.0.15 2. Excessive broadcasts are generally a symptom of a problem at which layer? physical data link network transport 3. Refer to the exhibit. Which three pieces of information can be determined by analyzing the output shown? (Choose three.) A carrier detect signal is present. Keepalives are being received successfully. Default encapsulation is used on this serial link. Packets passing this interface cannot exceed 1 KB in size. The reliability of this link is very low. The LCP negotiation phase is complete. 4. A network administrator has received complaints that users on a local LAN can retrieve e-mail from a remote e-mail server but are unable to open web pages on the same server. Services at which two layers of the OSI model should be investigated during the troubleshooting process? (Choose two.) physical layer data link layer network layer transport layer application layer 5. When gathering symptoms for troubleshooting a network problem, which step could result in getting an external administrator involved in the process? narrowing the scope gathering symptoms from suspect devices analyzing existing symptoms determining ownership 6. Encapsulation errors from mismatched WAN protocols on a serial link between two routers indicate a problem at which OSI layer? physical data link network transport 7. Refer to the exhibit. Users at Branch B are reporting trouble accessing a corporate website running on a server that is located at HQ. HQ and Branch A users can access the website. R3 is able to ping 10.10.10.1 successfully but not 10.10.10.2. The users at Branch B can access servers at Branch A. Which two statements are true aboutthe troubleshooting efforts? (Choose two.) The web server should be tested for an application layer problem. Frame Relay at R3 and R2 should be tested to narrow the scope of the problem. The fact that users at Branch A are working normally proves that there is no problem at R2. An ACL entry error could cause the failure at Layer 4 in either R3 or R2. The successful ping from R3 to R1 proves that the WAN is functioning normally. Therefore, the problem has to be in the upper layers. 8. Which troubleshooting approach is suggested for dealing with a complex problem that is suspected of being caused by faulty network cabling? bottom up top down divide and conquer middle out 9. Users are complaining of very long wait times to access resources on the network. The show interface command reveals collision counts far above the network baseline. At which OSI layer should the administrator begin troubleshooting? application transport network data link physical 10. Refer to the exhibit. Users on the Internal LAN are unable to connect to the www server. The network administrator pings the server and verifies that NAT is functioning correctly. Which OSI layer should the administrator begin to troubleshoot next? physical data link network application 11. Which two statements are true concerning logical networking models? (Choose two.) TCP/IP splits the lowest layer of the OSI model into two separate layers. The top layer of the TCP/IP model combines the functions of the top three OSI layers. Troubleshooting with the TCP/IP model requires different techniques than with the OSI model. The network access layer is responsible for exchanging packets between devices on a TCP/IP network. The Internet layer provides communication between applications, such as FTP, HTTP, and SMTP on separate hosts. The TCP/IP network access layer corresponds to the OSI physical and data link layers. 12. Refer to the exhibit. Which two steps should be taken during the process of creating network documentation? (Choose two.) Record the information about the devices discovered in the Campus network only. Record the information about the devices discovered in the entire network, including the remote locations. Transfer any information about the devices from the network configuration table that corresponds to a component of the topology diagram. Transfer only the Layer 2 and Layer 3 information about the devices from the network configuration table that corresponds to a component of the topology diagram. Transfer the recorded information about the devices from the network configuration table gathered during peak network utilization that corresponds to a component of the topology diagram. 13. What is one example of a physical layer problem? incorrect encapsulation incorrect STP configuration incorrect ARP mapping incorrect clock rate 14. Clients across the company are reporting poor performance across all corporate applications running in the data center. Internet access and applications running across the corporate WAN are performing normally. The network administrator observes a continual broadcast of random meaningless traffic (jabber) on the application server LAN in the data center on a protocol analyzer. How should the administrator start troubleshooting? The jabber in the data center indicates a local physical layer problem. Use the protocol analyzer to determine the source of the jabber, and then check for a recent NIC driver update or bad cabling. Because all clients are experiencing application problems, the administrator should use a top-down approach with the application servers in the data center. The scope of the problem indicates a likely routing or spanning-tree problem. Begin by checking routing tables, and follow up using appropriate STP show commands to find a loop if routing is working normally. Poll the staff to determine if any recent changes have been made. Back out all the changes one by one until the error condition is fixed. 15. A technician has been asked to make several changes to the configuration and topology of a network and then determine the outcome of the changes. What tool can be used to determine the overall effect caused by the changes? baselining tool knowledge base protocol analyzer cable tester 16. A technician has been asked to troubleshoot an existing switched network but is unable to locate documentation for the VLAN configuration. Which troubleshooting tool allows the technician to map and discover VLAN and port assignments? cable analyzer network analyzer protocol analyzer knowledge base 17. Which two pieces of information are typically found on a logical network diagram? (Choose two.) cable types connector types interface identifiers DLCI for virtual circuits operating system versions 18. Which two components should be taken into consideration when establishing a network baseline? (Choose two.) information about the network design IP addressing allocation on the network requirements about the service provider setup requirements for access control lists to regulate traffic expected performance under normal operating conditions 19. Which three approaches should be used when attempting to gather data from users for troubleshooting? (Choose three.) Determine fault. Get to know the user to build trust. Obtain information by asking simple pertinent questions. Impress the user with use of technical language and skills. Determine if the problem is related to time or a specific event. Determine if the user can re-create the problem or events leading to the problem. 20. Information about which OSI layers of connected Cisco devices can be verified with the show cdp neighbors command? All layers Layer 1, Layer 2, and Layer 3 Layer 1, Layer 2, Layer 3, and Layer 4 Layer 6 and Layer 7 | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Posted: 28 Dec 2010 05:20 PM PST 1. What functionality do access control lists provide in the implementation of dynamic NAT on a Cisco router? define which addresses can be translated define which addresses are assigned to a NAT pool define which addresses are allowed out the router define which addresses can be accessed from the inside network 2. Which three guidelines would help contribute to creating a strong password policy? (Choose three.) Once a good password is created, do not change it. Deliberately misspell words when creating passwords. Create passwords that are at least 8 characters in length. Use combinations of upper case, lower case, and special characters. Write passwords in locations that can be easily retrieved to avoid being locked out. Use long words found in the dictionary to make passwords that are easy to remember. 3. Refer to the exhibit. Every time the administrator reboots this router, the boot process ends in setup mode. What is a possible problem? There is insufficient RAM for the IOS to load on this router. A password recovery process should be done on this router. The bootstrap version and the version of the IOS are different. The IOS image is damaged and must be reloaded using tftpdnld. The configuration register is set to ignore the startup configuration. 4. Which option correctly defines the capacity through the local loop guaranteed to a customer by the service provider? BE DE CIR CBIR 5. Refer to the exhibit. A host connected to Fa0/0 is unable to acquire an IP address from the DHCP server. The output of the debug ip dhcp server command shows "DHCPD: there is no address pool for 10.1.1.1". What is the problem? The 10.1.1.1 address is already configured on Fa0/0. The default router for the 10Network pool is incorrect. The ip helper-address must be added to Fa0/0 interface. The pool of addresses for the 10Network pool is incorrect. 6. Which data link layer encapsulation protocol is used by default for serial connections between two Cisco routers? ATM Frame Relay HDLC PPP SDLC 7. Refer to the exhibit. Which statement correctly describes how Router1 processes an FTP request that enters interface s0/0/0 and is destined for an FTP server at IP address 192.168.1.5? The router matches the incoming packet to the statement that was created by the access-list 201 deny icmp 192.168.1.0 0.0.0.255 any command, continues comparing the packet to the remaining statements in ACL 201 to ensure that no subsequent statements allow FTP, and then the router drops the packet. The router reaches the end of ACL 101 without matching a condition and drops the packet because there is no statement that was created by the access-list 101 permit ip any any command. The router matches the incoming packet to the statement that was created by the access-list 101 permit ip any 192.168.1.0 0.0.0.255 command and allows the packet into the router. It matches the incoming packet to the statement that was created by the access-list 201 permit ip any any command and allows the packet into the router. 8. Compared with IDS systems, what can IPS systems do to provide further protection of computer systems? detect potential attacks stop the detected attack from executing update OS patches for computer systems scan computer systems for viruses and spyware 9. Which IEEE 802.16 broadband wireless technology allows users to connect to the ISP at speeds comparable to DSL and cable? Wi-Fi satellite WiMAX Metro Ethernet 10. A network administrator has changed the VLAN configurations on his network switches over the past weekend. How can the administrator determine if the additions and changes improved performance and availability on the company intranet? Conduct a performance test and compare with the baseline that was established previously. Interview departmental secretaries and determine if they think load time for web pages has improved. Determine performance on the intranet by monitoring load times of company web pages from remote sites. Compare the hit counts on the company web server for the current week to the values that were recorded in previous weeks. 11. Refer to the exhibit. What is the meaning of the term dynamic in the output of the command? The bandwidth capability of the interface increases and decreases automatically based on BECNs. The Serial0/0/1 interface acquired 172.16.3.1 from a DHCP server. The mapping between DLCI 100 and 172.16.3.1 was learned through Inverse ARP. DLCI 100 will automatically adapt to changes in the Frame Relay cloud. 12. Which type of ACL will permit traffic inbound into a private network only if an outbound session has already been established between the source and destination? extended reflexive standard time-based 13. Which two statements are true about IPv6 link local addresses? (Choose two.) They begin with the 2000::/3 prefix. They begin with the FE80::/10 prefix. They are assigned by IANA to an organization. They must be manually configured by the administrator. They are assigned to a host by a stateless autoconfiguration process. 14. A company is looking for a WAN solution to connect its headquarters site to four remote sites. What are two advantages that dedicated leased lines provide compared to a shared Frame Relay solution? (Choose two.) reduced jitter reduced costs reduced latency the ability to burst above guaranteed bandwidth the ability to borrow unused bandwidth from the leased lines of other customers 15. Refer to the exhibit. A network administrator is trying to connect R1 remotely to make configuration changes. Based on the exhibited command output, what will be the result when attempting to connect to R1? failure to connect due to Telnet not being enabled failure to connect due to incomplete configuration for Telnet a successful connection and ability to make configuration changes a successful connection but inability to make configuration changes because of the absence of an enable secret password 16. What are two effective measures for securing routers? (Choose two.) Protect all active router interfaces by configuring them as passive interfaces. Configure remote administration through VTY lines for Telnet access. Use quotes or phrases to create pass phrases. Disable the HTTP server service. Enable SNMP traps. 17. An issue of response time has recently arisen on an application server. The new release of a software package has also been installed on the server. The configuration of the network has changed recently. To identify the problem, individuals from both teams responsible for the recent changes begin to investigate the source of the problem. Which statement applies to this situation? Scheduling will be easy if the network and software teams work independently. It will be difficult to isolate the problem if two teams are implementing changes independently. Results from changes will be easier to reconcile and document if each team works in isolation. Only results from the software package should be tested as the network is designed to accommodate the proposed software platform. 18. Refer to the exhibit. From the output of the show interfaces and ping commands, at which layer of the OSI model is a fault indicated? application transport network data link physical 19. Which technology is used to dynamically map next hop, network layer addresses to virtual circuits in a Frame Relay network? Inverse ARP LMI DLCI FECN 20. An administrator learns of an e-mail that has been received by a number of users in the company. This e-mail appears to come from the office of the administrator. The e-mail asks the users to confirm their account and password information. Which type of security threat does this e-mail represent? cracking phishing phreaking spamming 21. Refer to the exhibit. Which data transmission technology is being represented? TDM PPP HDLC SLIP 22. Refer to the exhibit. Results of the show vlan and show vtp status commands for switches S1 and S2 are displayed in the exhibit. VLAN 11 was created on S1. Why is VLAN 11 missing from S2? There is a Layer 2 loop. The VTP domain names do not match. Only one switch can be in server mode. S2 has a higher spanning-tree priority for VLAN 11 than S1 does. 23. What is the result of adding the global command service password-encryption to the configuration of a router? Line passwords are encrypted with type 7 encryption. Enable passwords are encrypted with type 5 encryption. All services must provide an encrypted password to function. Only encrypted messages are allowed for router communication. 24. While troubleshooting a problem with an e-mail server, an administrator observes that the switch port used by the server shows "up, line protocol up". The administrator cannot ping the server. At which layer of the OSI model is the problem most likely to be found? application layer network layer data link layer physical layer 25. Where does a service provider assume responsibility from a customer for a WAN connection? local loop DTE cable on router demarcation point demilitarized zone 26. What will be the result of adding the command ip dhcp excluded-address 192.168.24.1 192.168.24.5 to the configuration of a local router that has been configured as a DHCP server? Traffic that is destined for 192.168.24.1 and 192.168.24.5 will be dropped by the router. Traffic will not be routed from clients with addresses between 192.168.24.1 and 192.168.24.5. The DHCP server will not issue the addresses ranging from 192.168.24.1 to 192.168.24.5. The router will ignore all traffic that comes from the DHCP servers with addresses 192.168.24.1 and 192.168.24.5. 27. Refer to the exhibit. Partial results of the show access-lists and show ip interface FastEthernet 0/1 commands for router Router1 are shown. There are no other ACLs in effect. Host A is unable to telnet to host B. Which action will correct the problem but still restrict other traffic between the two networks? Apply the ACL in the inbound direction. Apply the ACL on the FastEthernet 0/0 interface. Reverse the order of the TCP protocol statements in the ACL. Modify the second entry in the list to permit tcp host 172.16.10.10 any eq telnet . 28. Refer to the exhibit. The corporate network that is shown has been assigned network 172.16.128.0/19 for use at branch office LANs. If VLSM is used, what mask should be used for addressing hosts at Branch4 with minimal waste from unused addresses? /19 /20 /21 /22 /23 /24 29. Refer to the exhibit. RIPv2 has been configured on all routers in the network. Routers R1 and R3 have not received any RIP routing updates. What will fix the issue? Enable RIP authentication on R2. Issue the ip directed-broadcast command on R2. Change the subnet masks to 10.11.12.0/8 and 172.16.40.0/16 on R2. Enable CDP on R2 so that the other routers will receive routing updates. 30. Refer to the exhibit. This serial interface is not functioning correctly. Based on the output shown, what is the most likely cause? improper LMI type interface reset PPP negotiation failure unplugged cable 31. Which statement is true about PAP in the authentication of a PPP session? PAP uses a two-way handshake. The password is unique and random. PAP conducts periodic password challenges. PAP uses MD5 hashing to keep the password secure. 32. An administrator is configuring a dual stack router with IPv6 and IPv4 using RIPng. The administrator receives an error message when trying to enter the IPv4 routes into RIPng. What is the cause of the problem? When IPv4 and IPv6 are configured on the same interface, all IPv4 addresses are over-written in favor of the newer technology. Incorrect IPv4 addresses are entered on the router interfaces. RIPng is incompatible with dual-stack technology. IPv4 is incompatible with RIPng. 33. What is tunneling? using digital certificates to ensure that data endpoints are authentic creating a hash to ensure the integrity of data as it traverses a network using alternate paths to avoid access control lists and bypass security measures encapsulating an entire packet within another packet for transmission over a network 34. Which statement is true about NCP? Link termination is the responsibility of NCP. Each network protocol has a corresponding NCP. NCP establishes the initial link between PPP devices. NCP tests the link to ensure that the link quality is sufficient. 35. Refer to the exhibit. A network administrator is creating a prototype to verify the new WAN design. However, the communication between the two routers cannot be established. Based on the output of the commands, what can be done to solve the problem? Replace the serial cable . Replace the WIC on RA. Configure RA with a clock rate command. Issue a no shutdown interface command on RB. 36. Refer to the exhibit. Based on the output as shown, which two statements correctly define how the router will treat Telnet traffic that comes into interface FastEthernet 0/1? (Choose two). Telnet to 172.16.10.0/24 is denied. Telnet to 172.16.20.0/24 is denied. Telnet to 172.16.0.0/24 is permitted. Telnet to 172.16.10.0/24 is permitted. Telnet to 172.16.20.0/24 is permitted. 37. Which Frame Relay flow control mechanism is used to signal routers that they should reduce the flow rate of frames? DE BE CIR FECN CBIR 38. Refer to the exhibit. A network administrator configures a standard access control list on Router1 to prohibit traffic from the 192.168.0.0/24 network from reaching the Internet. The access control list also permits traffic from the 192.168.0.0/24 network to reach the 192.168.1.0/24 network. On which interface and in which direction should the access control list be applied? interface Fa0/0, inbound interface Fa0/0, outbound interface S0/0/0, inbound interface S0/0/0, outbound 39. Which configuration on the vty lines provides the best security measure for network administrators to remotely access the core routers at headquarters? 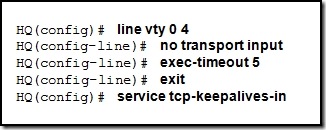 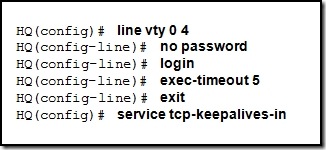 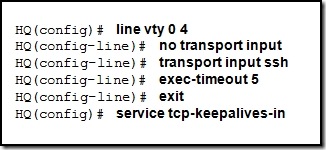 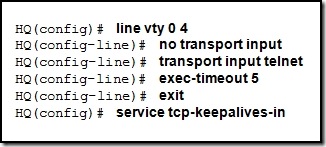 Answer: 3nd option 40. Refer to the exhibit. What can be concluded from the exhibited output of the debug ip nat command? The 10.1.1.225 host is exchanging packets with the 192.168.0.10 host. The native 10.1.200.254 address is being translated to 192.168.0.10. The 192.168.0.0/24 network is the inside network. Port address translation is in effect. 41. A network administrator is instructing a technician on best practices for applying ACLs. Which suggestion should the administrator provide? Named ACLs are less efficient than numbered ACLs. Standard ACLs should be applied closest to the core layer. ACLs applied to outbound interfaces are the most efficient. Extended ACLs should be applied closest to the source that is specified by the ACL. 42. Refer to the exhibit. Headquarters is connected through the Internet to branch office A and branch office B. Which WAN technology would be best suited to provide secure connectivity between headquarters and both branch offices? ATM VPN ISDN Frame Relay broadband DSL 43. Which three physical network problems should be checked when a bottom-up troubleshooting approach has been chosen to troubleshoot network performance? (Choose three.) cable connectivity high collision counts STP failures and loops address mapping errors high CPU utilization rates excess packets that are filtered by the firewall 44. Refer to the exhibit. A network administrator is attempting to configure a Frame Relay network. The administrator enters the commands as shown in the exhibit on R2, but the Frame Relay PVCs are inactive. What is the problem? The incorrect DLCI numbers are being configured on R2. The S0/0/0 interface on R2 needs to be point-to-point. The frame-relay map commands are missing the cisco keyword at the end. A single router interface cannot connect to more than one Frame Relay peer at a time. 45. Which IP address and wildcard mask would be used in an ACL to block traffic from all hosts on the same subnet as host 192.168.16.43/28? access-list 10 deny 192.168.16.0 0.0.0.31 access-list 10 deny 192.168.16.16 0.0.0.31 access-list 10 deny 192.168.16.32 0.0.0.16 access-list 10 deny 192.168.16.32 0.0.0.15 access-list 10 deny 192.168.16.43 0.0.0.16 46. Which combination of Layer 2 protocol and authentication should be used to establish a link without sending authentication information in plain text between a Cisco and a non-Cisco router? PPP with PAP PPP with CHAP HDLC with PAP HDLC with CHAP 47. When would the multipoint keyword be used in Frame Relay PVCs configuration? when global DLCIs are in use when using physical interfaces when multicasts must be supported when participating routers are in the same subnet 48. A network technician analyzes the network and notices late collisions. The collisions occur accompanied by jabber that originates from the server. What is the likely cause of the problem? faulty switch port web server CPU overload faulty NIC in the web server misconfiguration of web server services 49. Refer to the exhibit. R1 is performing NAT overload for the 10.1.1.0/24 inside network. Host A has sent a packet to the web server. What is the destination IP address of the return packet from the web server? 10.1.1.2:1234 172.30.20.1:1234 172.30.20.1:3333 192.168.1.2:80 50. Refer to the exhibit. All devices are configured as shown in the exhibit. PC1 is unable to ping the default gateway. What is the cause of the problem? The default gateway is in the wrong subnet. STP has blocked the port that PC1 is connected to. Port Fa0/2 on S2 is assigned to the wrong VLAN. S2 has the wrong IP address assigned to the VLAN30 interface. 51. When Frame Relay encapsulation is used, what feature provides flow control and exchanges information about the status of virtual circuits? LCP LMI DLCI Inverse ARP 52. A network administrator is tasked with maintaining two remote locations in the same city. Both locations use the same service provider and have the same service plan for DSL service. When comparing download rates, it is noticed that the location on the East side of town has a faster download rate than the location on the West side of town. How can this be explained? The West side has a high volume of POTS traffic. The West side of town is downloading larger packets. The service provider is closer to the location on the East side. More clients share a connection to the DSLAM on the West side. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Engineer,CCNA ATM VOIP Lan Wan Posted: 14 Jan 2010 05:47 PM PST Company Profile Subex Technologies offers Software Services for building and deploying products/ applications that help Telecom and Media service providers offer integrated, bundled and convergent services over IP networks including Media services like IPTV, Triple Play, and Interactive TV, etc. Job Details Title: Engineer,CCNA ATM VOIP Lan Wan Posted On: 1/12/2010 8:53:18 AM Designation: Engineer,CCNA ATM VOIP Lan WanNo. of vacancies: 1 Qualifications: 2 year degree desirable
Minimum Total Experience: 2 Job Tenure: No Preference/Any Salary Offered: Job Location: Piscataway, NJ United States Job Description Major ResponsibilitiesRender technical support to customers for all AST supported services. Analyze and resolve all customer circuit impairments Process Orders Manually configure switches and routers Perform Layer I, II, and III troubleshooting Support end-to-end Customer Test and Turn-up. Work with and support various internal organizations during pre/post deployment testing and pre-sales. Required Skills/Knowledge Familiarity with Cisco routers Understanding of IP and subnetting. Understanding of the OSI Model Ability to Multitask Time management Excellent written and verbal communication Exceptional Interpersonal Skills Ability to work independently and take ownership of troubles Aptitude for segmenting, diagnosing, and resolving complex troubles Desirable Skills/Knowledge Customer service experience Knowledge of FR, ATM, or DSL Frame and ATM Switches Education and Work Experience. 2 year degree desirable CCNA a plus Skill Experience Need 1) Switches and Routers Expert Required 2) Project Management Expert Required 3) Communication skills Expert Required 4) IP and subnetting Expert Required 5) Customer Service Expert Required 6) Frame and ATM Switches Expert Required 7) CCNA Expert Desired Source: http://www.careerjet.com/job/c383956fe359d6a34192ad4bb2e64c21.html | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| All Answer CCNA1, CCNA2, CCNA3, CCNA4, CCNA Final Posted: 16 Jan 2010 05:58 AM PST http://www.4shared.com/file/138281712/49a03690/CCNA1_chapter_1.html http://www.4shared.com/file/138281721/fb8434e9/CCNA1_chapter_2_v1.html http://www.4shared.com/file/138281726/65e0a14a/CCNA1_chapter_2_v2.html http://www.4shared.com/file/138281738/9b43bd0c/CCNA1_chapter_3_v1.html http://www.4shared.com/file/138281742/34d7c2d5/CCNA1_chapter_3_v2.html http://www.4shared.com/file/138281754/c4af56a1/CCNA1_chapter_4_v1.html http://www.4shared.com/file/138281759/ba1e2a1c/CCNA1_chapter_4_v2.html http://www.4shared.com/file/138281768/e6344949/CCNA1_chapter_5_v1.html http://www.4shared.com/file/138281770/f1f4f03a/CCNA1_chapter_5_v2.html http://www.4shared.com/file/138281777/6f906599/CCNA1_chapter_6_v1.html http://www.4shared.com/file/138281780/766cecf5/CCNA1_chapter_6_v2.html http://www.4shared.com/file/138281789/fb05451/CCNA1_chapter_7_v1.html http://www.4shared.com/file/138281792/8179bc98/CCNA1_chapter_7_v2.html http://www.4shared.com/file/138281802/5be740ec/CCNA1_chapter_8_v1.html http://www.4shared.com/file/138281811/dbf52017/CCNA1_chapter_8_v2.html http://www.4shared.com/file/138281816/4591b5b4/CCNA1_chapter_9_v1.html http://www.4shared.com/file/138281821/f0d873d4/CCNA1_chapter_10_v1.html http://www.4shared.com/file/138281824/80b2875b/CCNA1_chapter_11_v1.html http://www.4shared.com/file/138281829/fe03fbe6/CCNA2_chapter_1_v1.html http://www.4shared.com/file/138281832/70ca132f/CCNA2_chapter_2_v1.html http://www.4shared.com/file/138281838/901ffa31/CCNA2_chapter_2_v2.html http://www.4shared.com/file/138281847/4fe17167/CCNA2_chapter_3_v1.html http://www.4shared.com/file/138281852/2690b4a9/CCNA2_chapter_3_v2.html http://www.4shared.com/file/138281857/56fa4026/CCNA2_chapter_4_v1.html http://www.4shared.com/file/138281860/e3b38646/CCNA2_chapter_4_v2.html http://www.4shared.com/file/138281868/ed680e74/CCNA2_chapter_4_v3.html http://www.4shared.com/file/138281874/fdc5731e/CCNA2_chapter_5_v1.html http://www.4shared.com/file/138281881/a379b5e/CCNA2_chapter_5_v2.html http://www.4shared.com/file/138281884/7a5d6fd1/CCNA2_chapter_6_v1.html http://www.4shared.com/file/138281888/73eb23fa/CCNA2_chapter_6_v2.html http://www.4shared.com/file/138281889/4ec136c/CCNA2_chapter_6_v3.html http://www.4shared.com/file/138281893/fd22cb33/CCNA2_chapter_7_v1.html http://www.4shared.com/file/138281897/fa4f0f2a/CCNA2_chapter_7_v2.html http://www.4shared.com/file/138281905/c441bf78/CCNA2_chapter_8_v1.html http://www.4shared.com/file/138281910/ad307ab6/CCNA2_chapter_8_v2.html http://www.4shared.com/file/138281913/34392b0c/CCNA2_chapter_10_v1.html http://www.4shared.com/file/138281912/433e1b9a/CCNA2_chapter_9_v1.html http://www.4shared.com/file/138281918/a3ebf284/CCNA2_chapter_11_v1.html http://www.4shared.com/file/138281923/1f1478cf/CCNA3_chapter_1_v1.html http://www.4shared.com/file/138281926/6f7e8c40/CCNA3_chapter_1_v2.html http://www.4shared.com/file/138281935/ef6cecbb/CCNA3_chapter_2_v1.html http://www.4shared.com/file/138281945/a02d7a7c/CCNA3_chapter_2_v2.html http://www.4shared.com/file/138281951/be5b8f24/CCNA3_chapter_3_v1.html http://www.4shared.com/file/138281956/203f1a87/CCNA3_chapter_3_v2.html http://www.4shared.com/file/138281974/fc071929/CCNA3_chapter_4_v1.html http://www.4shared.com/file/138281979/82b66594/CCNA3_chapter_4_v2.html http://www.4shared.com/file/138281988/722949cd/CCNA3_chapter_4_v3.html http://www.4shared.com/file/138281992/8be79192/CCNA3_chapter_5_v1.html http://www.4shared.com/file/138281997/fb8d651d/CCNA3_chapter_5_v2.html http://www.4shared.com/file/138282002/4741beba/CCNA3_chapter_6_v1.html http://www.4shared.com/file/138282008/a79457a4/CCNA3_chapter_6_v2.html http://www.4shared.com/file/138282011/c753de41/CCNA3_chapter_7_v1.html http://www.4shared.com/file/138282012/5e5a8ffb/CCNA3_chapter_7_v2.html http://www.4shared.com/file/138282021/ec7e8d82/CCNA4_chapter_1_v1.html http://www.4shared.com/file/138282026/721a1821/CCNA4_chapter_2_v1.html http://www.4shared.com/file/138282031/f565bcc3/CCNA4_chapter_3_v1.html http://www.4shared.com/file/138282039/fbbe34f1/CCNA4_chapter_4_v1.html http://www.4shared.com/file/138282043/542a4b28/CCNA4_chapter_5_v1.html http://www.4shared.com/file/138282046/2440bfa7/CCNA4_chapter_7_v1.html http://www.4shared.com/file/138282051/a33f1b45/CCNA4_chapter_8_v1.html | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Redistribution : Rip & OSPF Using Packet Tracer Posted: 28 Sep 2010 08:29 AM PDT I was playing around with Packet Tracer today, thought why not give it a try. Nice program none the less. So here is a very modest try on basic redistribution. I thought it will help someone. The lab had very basic set up, i used three routers and with a bunch of loopbacks i tested the redistribution between RIP and OSPF. You can use this lab as a tester or a reference point. PT lacks a lot of command options but is still very highly usable. So here is the setup: Router 1: (RIP V2) interface Loopback1 ip address 192.168.10.100 255.255.255.0 ! interface Loopback2 ip address 2.2.2.2 255.0.0.0 ! interface Serial0/0 ip address 172.16.10.1 255.255.255.252 ! router rip version 2 network 2.0.0.0 network 172.16.0.0 network 192.168.10.0 no auto-summary Router 3: (OSPF 1) interface Loopback1 ip address 3.3.3.3 255.0.0.0 ! interface Loopback2 ip address 192.168.20.100 255.255.255.0 ! interface Serial0/0 ip address 172.16.20.1 255.255.255.252 clock rate 64000 ! router ospf 1 log-adjacency-changes network 3.3.3.3 0.0.0.0 area 0 network 192.168.20.0 0.0.0.255 area 0 network 172.16.20.0 0.0.0.3 area 0 Router 2: (Performed the redistribution) interface Serial0/0 ip address 172.16.10.2 255.255.255.252 clock rate 64000 ! interface Serial0/1 ip address 172.16.20.2 255.255.255.252 ! router ospf 1 log-adjacency-changes redistribute rip subnets network 172.16.20.0 0.0.0.3 area 0 ! router rip version 2 redistribute ospf 1 metric 5 network 172.16.0.0 no auto-summary Outputs: Router 1: (Rip) Gateway of last resort is not set C 2.0.0.0/8 is directly connected, Loopback2 3.0.0.0/32 is subnetted, 1 subnets R 3.3.3.3 [120/5] via 172.16.10.2, 00:00:01, Serial0/0 172.16.0.0/30 is subnetted, 2 subnets C 172.16.10.0 is directly connected, Serial0/0 R 172.16.20.0 [120/1] via 172.16.10.2, 00:00:01, Serial0/0 C 192.168.10.0/24 is directly connected, Loopback1 192.168.20.0/32 is subnetted, 1 subnets R 192.168.20.100 [120/5] via 172.16.10.2, 00:00:01, Serial0/0 Router 3: (OSPF) O E2 2.0.0.0/8 [110/781] via 172.16.20.2, 00:18:56, Serial0/0 C 3.0.0.0/8 is directly connected, Loopback1 172.16.0.0/30 is subnetted, 2 subnets O E2 172.16.10.0 [110/781] via 172.16.20.2, 00:18:56, Serial0/0 C 172.16.20.0 is directly connected, Serial0/0 O E2 192.168.10.0/24 [110/781] via 172.16.20.2, 00:18:56, Serial0/0 C 192.168.20.0/24 is directly connected, Loopback2 Router 2: (Performed Redistribution) R 2.0.0.0/8 [120/1] via 172.16.10.1, 00:00:00, Serial0/0 3.0.0.0/32 is subnetted, 1 subnets O 3.3.3.3 [110/782] via 172.16.20.1, 00:20:15, Serial0/1 172.16.0.0/30 is subnetted, 2 subnets C 172.16.10.0 is directly connected, Serial0/0 C 172.16.20.0 is directly connected, Serial0/1 R 192.168.10.0/24 [120/1] via 172.16.10.1, 00:00:00, Serial0/0 192.168.20.0/32 is subnetted, 1 subnets O 192.168.20.100 [110/782] via 172.16.20.1, 00:20:15, Serial0/1 (The routes that are in bold are learned using redistribution) Now you could use the "passive-interface" command on s0/1 of Router 2 so that route on s0/1 is advertised by RIP. If you want the PT lab file, here is the link: hxxp://[nofileshares].com/files/195399030/redist-lab1.pkt.html Note: As i mentioned above PT does lack some of the advance features. For example while redistributing the rip i was not able to specify the metric-type. But as you can see it still works. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| TCL Scripting in IOS. Easy to understand Tutorial ! Posted: 29 Sep 2010 06:31 AM PDT Hi all. Here i am with yet another tutorial. Programming in IOS. Dont confuse it with programming IOS because you cant do it. IOS is not open source so you cant make extensions/modifications to it, But IOS allows you to use TCL (pronounced "tickle") scripting language to write scripts to get tasks done in a different and more feasible way, that was either not possible before or too complicated. One example is the recent query posted by our fellow member superr about how to monitor snmp OID to trigger events. Although the solution was in EEM, but the same could be done using tcl. Those who are totally new to this stuff will be getting confused as to what i am talking about. So lets see a few examples, that are very practical and you may encounter tasks similar to these more often. Example 1) When router cpu utilization reaches 30%, send an email to me, plus give only the first five top processes in "sh process cpu sorted". Example 2) (this is a case of ARP flooding/looping which causes the router to nearly crash) If router cpu utilization reaches above 80%, check the current processes to see if the top 2 processes contains ARP-Input, if this is the case, check the show int to see which interface is getting lots of broadcast. Find the interface and shut it down, Wait for 3 mins and recheck the process level to see if its ok (below 80%), if yes then check the WAN link to reach the email server, if the wan link is reachable, send an email to notify the support engineer that this event has occurred !! (dont get your head spinning, there's a lot more to follow ;-)) Example 3) You have 200+ routers in your access. You want to make sure that every WAN interface is configured with IPsec VPN. Considering 2 WAN links per router means checking of 400 interfaces, can you do that by 1) manually opening the router and viewing the running config ? 2) manually opening the backup config stored on your pc and viewing it ? 3) Or simply open the router, paste the tcl script, that will do all the checking, in the end telling you which interfaces are not vpn enabled and optionally enabling the IPSEC vpn on them !! Depending on your views, these example might be appealing and might not. But if you are network administrator of 100+ routers, then i consider scripting/EEM to be a must-know knowledge, SIMPLE !!. There is no option, you must learn it. It gives you more control and chances of your completing complicated tasks increase dramatically. I would recommend the following books to learn more about tcl and how to program. Tcl and Tk Programming for the Absolute Beginner Hello World!: Computer Programming for Kids and Other Beginners by Warren Sande and Carter Sande (its for python) But remember, i have spend 4 years in my BS doing programming, and no book can teach you how to program. They will at best simply teach the syntax of the programming language but wont teach you, how to solve your problems using programming language. So you need to do a lot of practice in order to become a good programmer. Remember, scriping in IOS doesnt require or expects that you start building robotic arms, or robots that speak by themselves, no automatic cars are required, NOTHING !!!!!. Q) So what the hell i will be doing ? A) Trust me or not, most of the time, you will be required to do string parsing, extracting your desired result, comparing it with some predefined value and doing some action. Thats it !! Q) Is it really that simple, or you think i am a dumbo ? A) It is !! Q) I dont trust you, na na.... A) Then just read on, i hope i will convince you on the way :-) Q) What if i am not convinced ? A) You will, trust me on that ;-) NOTE: this entire tutorial will be very very specific to scripting in IOS. Remember that. Some of the programming essentials ! Programming is same as scripting. I may use the word program and script interchangebly, so dont get confused, they are the same thing. Variables. Variables are fundamental in every programming language. You will never see a language without variables, and perhaps not a single proper program written without using variables. NEVER !! Variables are simply places to hold values. Consider this myfirstvar = 4 over here, the name of variable is "myfirstvar" and the value of this variable is 4. simple :-). Q) Hey hey, what simple ? whats simple about this ? when and why i will be using variables ? A) You will use variables under two conditions 1) When you are taking input from the user 2) When you need to use a same value more then "1" time in your program. User input must be kept somewhere, so for that purpose its necassary to use variables or more properly storage areas. Now before going into detail, lets see tcl in your router. login to your router and type tclsh from exec mode. Printing on screen. R1# tclsh R1(tcl)# puts "hi, i am in tcl :-)" hi, i am in tcl :-) R1(tcl)# "puts" keyword simply displays what ever is given under inverted commas on screen. Variables. R1(tcl)# set myfirstvar 10 10 R1(tcl)# Over here, "set" is use to assigned a variable "myfirstvar" some value, which in this case is number "4". Now to print the variable do this, R1(tcl)# puts myfirstvar myfirstvar R1(tcl)# Now this was not i expected. the variable "myfirstvar" is simply a place to store the values. So if you have a locker in bank, then the stuff in that locker is important and not the locker. So variable is the locker, the value is the stuff you place in that locker. So to get the value inside myfirstvar, you have to put the dollar sign in front of it.. R1(tcl)# puts $myfirstvar 10 R1(tcl)# Now lets create 2 variables, assign them numbers and add them. To do mathematical calculations, tcl uses keyword "expr" R1(tcl)#set var1 100 100 R1(tcl)#set var2 200 200 R1(tcl)#set var3 [expr $var1 + $var2] 300 R1(tcl)#puts $var3 300 R1(tcl)# over here "[expr $var1 + $var2]", $var1 says to tcl, that use the value kept in var1 which is 100. $var2 tells to use the value kept in var2 which is 200. expr tells tcl to perform the addition (or whatever like subtraction, multiplication, division, exponentiation). "[]" square brackets will be replaced with whatever value is calculated inside them, so the above expression is more like this R1(tcl) set var3 300 [expr $var1 + $var2] gives value 300, which will be replaced with it and appears like above statement. We will be using square brackets alot so dont be confused. In Tcl, you can execute IOS commands as well using following 2 keywords 1) exec -> to run privilege mode commands 2) ios_config -> to run all config mode commands. Using Exec command R1(tcl)#exec sh ip int brief Interface IP-Address OK? Method Status Prot ocol Serial1/0 unassigned YES unset administratively down down Serial1/1 unassigned YES unset administratively down down Serial1/2 unassigned YES unset administratively down down Serial1/3 unassigned YES unset administratively down down R1(tcl)# Using ios_config command R1(tcl)# ios_config "int serial 1/0" "ip address 11.0.0.1 255.255.255.252" "no shut" R1(tcl)#exec show ip int brief Interface IP-Address OK? Method Status Prot ocol Serial1/0 11.0.0.1 YES unset up up Serial1/1 unassigned YES unset administratively down down Serial1/2 unassigned YES unset administratively down down Serial1/3 unassigned YES unset administratively down down R1(tcl)# Note: While in tcl mode, you can run IOS commands directly without these keywords, but as we go deeper, you will understand why these keywords make a difference. Now lets create a simple tcl program. Program 1) Create a tcl program to calculate the DRAM on your router. Now lets see how to write a program. 1) First solve it on paper and follow the steps carefully, observe deeply how exactly did you solved this issue. I would solve it like this First i will do "show version" R1#sh ver Cisco IOS Software, 3600 Software (C3640-JS-M), Version 12.4(12), RELEASE SOFTWA RE (fc1) Technical Support: http://www.cisco.com/techsupport Copyright © 1986-2006 by Cisco Systems, Inc. Compiled Fri 17-Nov-06 13:59 by prod_rel_team ROM: ROMMON Emulation Microcode ROM: 3600 Software (C3640-JS-M), Version 12.4(12), RELEASE SOFTWARE (fc1) R1 uptime is 1 hour, 21 minutes System returned to ROM by unknown reload cause - suspect boot_data[BOOT_COUNT] 0 x0, BOOT_COUNT 0, BOOTDATA 19 System image file is "tftp://255.255.255.255/unknown" Cisco 3640 (R4700) processor (revision 0xFF) with 116736K/6144K bytes of memory. Processor board ID 00000000 R4700 CPU at 100MHz, Implementation 33, Rev 1.2 4 Serial interfaces DRAM configuration is 64 bits wide with parity enabled. 125K bytes of NVRAM. 8192K bytes of processor board System flash (Read/Write) Configuration register is 0x2142 --More-- I will locate the line in bold. then i will add both values i.e. 116736 and 6144 and to convert it to MB, divide it by 1024, which gives me the value of 120. (i am using dynamips and have given exactly 120 ram, so this calculation producess perfect result :-) ). Now remember, machines are simply dumb, you need to tell them each and everything to solve the issue, because whether you realize it or not, you also require all the pieces together in order to solve the issue. You can sure make some assumptions, but that assumption is usually not completely random, its always based on some prior knowledge. But in case of computers, you have to tell them everything. Now lets break the above solution to MOST SIMPLISTIC STEPS. 1) Run the command show version 2) locate the line which contains the value i.e. 116737k/6144 3) Add both the values before and after "/" 4) Divide them by 1024 5) Display the result Now as you can see, these steps cant be further broken down. Now lets solve them 1 by 1, 1) set version [exec show version] Now for second step, we have to go a bit more DEEPER. Here starts the most important topic PARSING THE GIVEN INPUT FOR A SPECIFIC STRING. Q) whats a string ? A) String is the collection of characters. Everything you type whether a number or a letter is essentially a character. So what ever we type, if it contains more then 1 character, it will become string. So this whole tutorial can be thought of a very large string. Q) what do you mean by parsing the string ? A) Parsing the string means, going through the string looking for something. Like in our case, i will parse (look through) show version output to locate the line containing the DRAM values. So how to search in a given string ?. There are usually 2 methods that i use 1) Taking the input, splitting it till i get to the value i want. 2) Using regular expression. I wont be using method 1 till i have no other way. In start i used it alot but you will realize as i did, its better to get comfortable with regular expressions. They are fast and easy way to search for a given string. CCNP guys must have played with BGP and surely regexp. Those who havent, you must do it. I will be giving a brief tutorial on how to use regexp. Q) What are regular expression ? A) They are more general/dynamic way of respresenting a given string. Q) Oh yeah !!! i know i am being dumb but it actually went over my head you know ! A) Ok so just read on. Lets consider the essentials of regular expression . means anything. Including space, newline, anything * means zero or more occurence of the character preceding this. + means one or more occurence of the character preceding it. - defines the range [] encloses the range Q) ..... WHAT ??? i have seen regexp and they are lot more, you are cheating !!!!!! A) Explanining regexp is not a part of this tutorial. I will be using a simplified approach to use regular expressions. Lets practice it a bit suppose i am giving you the following string Hi, my height is 100 foot 11 inches. My color is fair, i have bright blue eyes and shiny hairs. Yesterday i had fever measuring 100. WOW !! Q) Are you talking about yourself ? A) Ofcourse not... Now using regular expression, EXTRACT the fever value. Now, focus the surrounding of the value you need to extract. "Yesterday i had fever measuring 100. WOW !!" and ALSO "Hi, my height is 100 foot 11 inches" We need the second 100 value thats after word "measuring". So in my opinion, i will tell the regexp to get me the value that is after "measuring ". Rest is all garbage right ? So in regexp, you must define what is garbage for you and what part is important. In our case, all what is before "measuring" is garbage, and all after 100 is garbage too. Garbage in regexp is denoted by ".*" . means anything and * means zero or more times. So it becomes anything (zero or more)times . * so our partial regular exp becomes .* measuring keep in mind, that we want to write a general expression so that it will give us any value that comes after measuring. Since this value (fever) is expected to change (since i am telling you !!), you have to generalize this using regexp. Fever value will always be a number. its length would be 2 - 3 digits ( am i right ?) ) so regular expression for fever value might be [0-9][0-9][0-9] TADAAAAAAAAAAAAAAAAAAAAA!!!! Nope its wrong. This may evaluate too First[0-9] = 1 Second[0-9] = 0 Third[0-9] = 0 This is right but not 100%. Fever values are usually like 98,99,100,102,104 etc. So the more appropriate regexp would be [0-9]+ Now, this says that number from 0-9 can appear more then once. Strictly speaking, it satisfies our need. But what if a value is given with 4 digits ?, or extremely high fever like 300 which is not possible, so let me give you a relief that, we wont be going into that much complication. AS long as we are able to extract our needed value out of given input, we are fine. So the complete regular expression becomes ".*measuring [0-9]+\." Q) Why have you written "\." ? A) As you know that "." is the regexp itself. I wanted to write period as it was appearing in statement, so for this purpose i add "\" telling the regexp that period is the literal value and not a regexp. Same is true for other regexp such as +,* etc. When you need to specify them as literals, just place a "\" before them. Now the syntax for tcl is as follows first lets assign this whole statement to a variable. R1(tcl)#set var1 "Hi, my height is 100 foot 11 inches. My color is fair, i hav$ Hi, my height is 100 foot 11 inches. My color is fair, i have bright blue eyes a nd shiny hairs. Yesterday i had fever measuring 100. WOW !! R1(tcl)# R1(tcl)# regexp {.*measuring ([0-9]+)\.} $var1 complete_string fever_value 1 <- 1 means match was found. 0 means match wasnt found R1(tcl)# puts $fever_value 100 R1(tcl)# Now lets see the syntax. Regular expression is written after regexp keyword and in curly braces. The value you need to actually extract is placed with round brackets within those curly braces. Then you place the variable containing the string that will be evaluated by the regexp followed by yet 2 more variables. The first variable will contain the complete string (which is useless to us) and second variable contains the value that will be extracted by the round brackets, which in our case will be value 100 as show in above example. Now lets get back to our example of extracting DRAM values from the entire show version string. First just pick up the line contaning the values. "Cisco 3640 (R4700) processor (revision 0xFF) with 116736K/6144K bytes of memory." Now if you have multiple platform, then the first value "Cisco 3640" is likely to change. Just run sh version on couple of routers and see which part of this line always remain constant. In my view it was the last 3 words " bytes of memory". You can verify this by looking at the entire ouput and making sure that these 3 words dont appear anywhere else, thus making this line unique. Now first try to write your own regexp for this. . . . . . . . . . Well, mine is ".*([0-9]+)K/([0-9]+)K bytes of memory." R1(tcl)#regexp {.*with ([0-9]+)K/([0-9]+)K bytes of memory.} $version complete_string first_val second_val 1 R1(tcl)#puts $first_val 116736 R1(tcl)#puts $second_val 6144 R1(tcl)# Now add them and divide them with 1024 to get the final result R1(tcl)#puts "the DRAM is [expr ($first_val + $second_val) / 1024]" the DRAM is 120 R1(tcl)# If you want to test this before hand, paste the following lines once you are in privilege mode --------------------------------------------------- tclsh set version [exec show version] regexp {.*with ([0-9]+)K/([0-9])+K bytes of memory.} $version complete_string first_val second_val puts "the DRAM is [expr ($first_val + $second_val) / 1024]" Check to see, if you get the correct output or not :-). --------------------------------------------------- Now, instead of going any further, just practice the above, by extracting different strings from different inputs. Like for example, extract the following from the show version output 1) IOS name 2) Model name 3) How much Flash 4) Configuration register value. Trust me, it just needs a practice of 1 or 2 days. We will move on once you are bit comfortable with regexp, since we will be using them alot. There would be rarely a script that will be written without them. This is just the start. These are not TCL based EEM scripts but they use similar logic. I will be writing more if you guys are getting what i am explaining here. Just give it a little effort and you will never regret it. Let me know of your feedback so i may write more. Plus, in your feedback, provide the regexp (complete scripts) for extracting all the 4 values i mentioned so i will also tell me that you actually learned something from this tutorial :-) | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Posted: 07 Sep 2010 06:05 PM PDT | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Posted: 21 Oct 2010 06:57 AM PDT Link to this site if you copy my content. Thank Petter ! 1. Which security protocol or measure would provide the greatest protection for a wireless LAN? WPA2 cloaking SSIDs shared WEP key MAC address filtering 2. Refer to the exhibit. All trunk links are operational and all VLANs are allowed on all trunk links. An ARP request is sent by computer 5. Which device or devices will receive this message? only computer 4 computer 3 and RTR-A computer 4 and RTR-A computer 1, computer 2, computer 4, and RTR-A computer 1, computer 2, computer 3, computer 4, and RTR-A all of the computers and the router 3. Refer to the exhibit. Hosts A and B, connected to hub HB1, attempt to transmit a frame at the same time but a collision occurs. Which hosts will receive the collision jamming signal? only hosts A and B only hosts A, B, and C only hosts A, B, C, and D only hosts A, B, C, and E 4. Refer to the exhibit. Router RA receives a packet with a source address of 192.168.1.65 and a destination address of 192.168.1.161. What will the router do with this packet? The router will drop the packet. The router will forward the packet out interface FastEthernet 0/1.1. The router will forward the packet out interface FastEthernet 0/1.2. The router will forward the packet out interface FastEthernet 0/1.3. The router will forward the packet out interface FastEthernet 0/1.2 and interface FastEthernet 0/1.3. 5. Refer to the exhibit. Which two settings show the default value of VTP configuration on a Cisco 2960 switch? (Choose two.) revision number existing VLANs operating mode domain name pruning mode 6. Which value determines if a switch becomes the central point of reference in the spanning tree topology? lowest bridge ID highest revision number lowest numeric IP address highest numeric MAC address 7. What is the purpose of the Spanning Tree algorithm? It propagates VLAN configurations to other switches. It restricts broadcast packets to a single VLAN. It segments a network into multiple broadcast domains. It prevents loops in a switched network with redundant paths. 8. What are two benefits of the IEEE 802.11n standard over the IEEE 802.11G? (Choose two.) requires less equipment provides improved range permits increased data rates has a single-input and a single-output needs no hardware upgrade for compatibility 9. Which configuration changes will increment the configuration revision number on the VTP server? configuring trunk links on the VTP server configuring or changing the VTP password configuring or changing the VTP domain name configuring or changing the VTP version number configuring or deleting a VLAN or creating a VLAN name 10. Refer to the exhibit. A company has acquired a new office in a campus environment. Switches in the existing office and the new office are directly connected by a trunk link. The VLANs and IP addressing are setup as shown in the exhibit. The computers in each office are not able to ping each other. What will fix the problem? Use an access link between S2 and S3. Connect S2 and S3 to a common router. Set the subnet mask in the new office to /24. Configure the new office default gateway to 172.17.10.1 Change the port assignments in the new office to a different VLAN. 11. What is a possible impact of setting too short an aging time in the MAC address table of a switch? overly large address table unnecessary flooding of packets excessive timeouts of static addresses impaired ability to dynamically learn new addresses 12. Refer to the exhibit. The network administrator has just added VLAN 50 to Switch1 and Switch2. Hosts A, B, C, and D are correctly configured with IP addresses in the subnet range for VLAN 50. Host A can communicate with host B, but cannot communicate with host C or host D. What is the cause of this problem? There is a native VLAN mismatch. The Fa0/11 interface of Switch1 is not configured as a trunk. The link between Switch1 and Switch2 is up but not trunked. VLAN 50 is not allowed on the trunk link between Switch1 and Switch2. 13. Refer to the exhibit. Users complain that they do not have connectivity to the web server that is connected to SW1. What should be done to remedy the problem? Allow all VLANs on the trunk link. Configure VLAN 100 as the native VLAN for SW1. Configure the trunk port in trunk mode on SW1. Attach the web server to a router and configure inter-VLAN routing. 14. What VLANs are allowed across a trunk when the range of allowed VLANs is set to the default value? only the management VLAN all VLANs except the extended range VLANs all VLANs except 1 and 1002-1005 all VLANs 15. Refer to the exhibit. A new host needs to be connected to VLAN 1. Which IP address should be assigned to this new host? 192.168.1.11 /28 192.168.1.22 /28 192.168.1.33 /28 192.168.1.44 /28 192.168.1.55 /28 16. Using the command copy tftp:backup.cfg startup-config, an administrator downloaded a saved configuration from a TFTP server to a switch. Why does the administrator not detect any changes in the switch configuration after the download completes? The command should have been copy startup-config tftp:backup.cfg. A backup configuration from a TFTP server cannot be copied directly into the startup-config. The command copy running-config startup-config should be used to save the changes on the switch. Downloading to the startup-config requires the switch to be reloaded in order for the configuration to take effect. 17. What two methods can be used to remove MAC address table entries from a switch? (Choose two.) Power cycle the switch to clear all dynamically learned addresses. The clear switching-tables command will remove statically configured entries. The clear mac-address-table command will remove statically and dynamically configured table entries. The erase flash command will clear all statically configured table entries. Statically configured MAC addresses will automatically be removed from the address table 300 minutes after the last activity on a switch port. 18. Which type of traffic can still be received on a switch interface that is in STP blocking mode? BPDU frames multicast frames broadcast frames Layer 3 packets 19. Which method establishes an administrative connection for configuring the Linksys WRT300N wireless access point? Associate with the access point and then open a HyperTerminal session with the access point. Physically connect to the access point and then reboot the computer to launch the configuration software. From a computer in the same IP subnet as the access point, enter the default IP address of the access point in a web browser. Modify the TCP/IP properties of the computer connected to the access point so that it exists on the same network, and then reboot your computer to establish a connection. 20. Refer to the exhibit. All edge ports are configured with the spanning-tree portfast command. Host1 is recently connected to port Fa0/1 on switch SW1 . Which statement is true about the status of port Fa0/1? The port will transition into blocking state. The port will transition immediately into forwarding state. The port will transition into blocking state and then immediately into forwarding state. The port will transition into blocking state and immediately transition through the listening and learning states. 21. Refer to the exhibit. What is true of the configuration of switch S1? A Cisco proprietary protocol is in use for ports Fa0/1 and Fa0/3. Switch ports Fa0/1 and Fa0/3 have been configured with the switchport mode access command. Untagged frames received on ports Fa0/1 and Fa0/3 will be placed on VLAN 1. Switch ports Fa0/1 and Fa0/3 are configured to carry data from multiple VLANs. 22. Refer to the exhibit. The configuration steps that are listed in the exhibit have been entered in switch S1 via the console. Subsequent attempts to telnet to the switch are not successful. What is causing the problem? The switch must be configured with SSH version 1. The transport input command must specify Telnet access. The RSA keys must be returned to zero before SSH will permit Telnet access. The ip domain-name command must also be entered in line configuration mode for the vty lines. 23. Refer to the exhibit. Which switch will be elected as the root bridge of the spanning tree topology? Cat-A Cat-B Cat-C Cat-D 24. Refer to the exhibit. VTP has been configured with VTP pruning enabled on all switches. If HostA sends a broadcast frame to SW1, which devices will receive the frame? SW1, SW3, HostF SW1, HostB, HostC SW1, SW2, SW3, SW4, HostF SW1, SW2, SW3, SW4, all hosts 25. Refer to the exhibit. Which two statements are true about the operation of the interfaces? (Choose two.) Incoming traffic with VLAN ID 0 is processed by interface fa0/0. Incoming traffic that has a VLAN ID of 2 is processed by subinterface fa0/0.2. Both subinterfaces remain up with line protocol up, even if fa0/0 line protocol is down. Subinterfaces use unique MAC addresses by adding the 802.1Q VLAN ID to the hardware address. Traffic inbound on this router is processed by different subinterfaces, depending on the VLAN from which the traffic originated. 26. The network administrator wants to configure a switch to pass VLAN update information to other switches in the domain but not update its own local VLAN database. Which two steps should the administrator perform to achieve this? (Choose two.) Reset the VTP counters. Configure VTP version 1 on the switch. Configure the VTP mode of the switch to transparent. Verify that the switch has a higher configuration revision number. Configure the switch with the same VTP domain name as other switches in the network. 27. 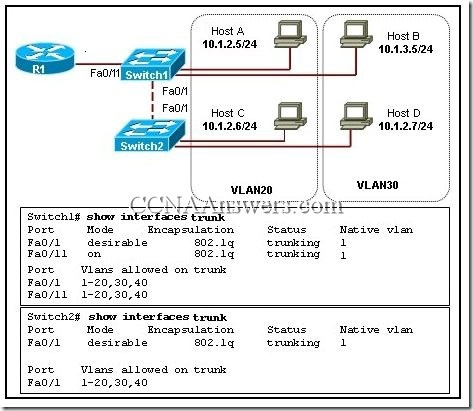 Refer to the exhibit. The devices in the network are operational and configured as indicated in the exhibit. However, hosts B and D cannot ping each other. What is the most likely cause of this problem? The link between the switches is up but not trunked. The Fa0/11 interface of Switch1 is not configured as a trunk. Hosts B and D are configured with IP addresses from different subnets. VLAN 20 and VLAN 30 are not allowed on the trunk between the switches. 28. Refer to the exhibit. Users A and B are reporting intermittent connectivity problems. Pre-installation surveys showed strong signal strength from the AP locations to the client locations. Outside electrical interference has been eliminated. What will fix the problem? Relocate the APs closer to each other. Increase the distance between the clients. Change the channel on AP-B to 6 or 11. Place AP-A and AP-B on the same wireless channel. 29. Why is it advisable that a network administrator use SSH instead of Telnet when managing switches? SSH uses TCP whereas Telnet does not. SSH encrypts only the username and password when logging in. SSH encrypts all remote management communications whereas Telnet does not. SSH sends a clear text message steam which reduces the bandwidth use for management. 30. Refer to the exhibit. The teacher host is connected to port Fa0/7 on switch STW. A student has decided to share access to the Internet by attaching a hub and laptop to STW as shown. What will be the result of the student making this connection? The Fa0/7 port of STW will be shutdown. The student will gain full access to the Internet. Both the teacher and student will be able to receive data but only the teacher will be able to send. The frames from the laptop will be dropped, but the teacher host will maintain connectivity with the network. 31. A network administrator configures a switch port with the command switchport mode dynamic auto. What is the resulting behavior of the switch port? The switch port is able to trunk if the remote switch port is set to auto. The switch port is able to trunk if the remote switch port is set to desirable. The switch port will be disabled if it is unable to successfully negotiate trunking. A successful trunk will be established if the remote switch is non-Cisco but the port is configured for trunking. 32. Which STP port type can only appear once on a segment, and must be present in order for traffic to flow on that segment? non-root port disabled port designated port non-designated port 33. Refer to the exhibit. What would happen if the network administrator moved the network cable of Host A from interface Fa0/1 to Fa0/3 on switch SW1? Host A remains a member of VLAN 10, because the router is routing traffic between VLANs. Host A is no longer a member of VLAN 10, because port Fa0/3 has been manually assigned to VLAN 30. Host A remains a member of VLAN 10, because the switch provides dynamic VLAN assignment for the port. Host A maintains connectivity to all members of VLAN 10, because it is connected to the same physical network. Host A is no longer a member of VLAN 10, but because port Fa0/3 was unused, it is now a member of VLAN 1. 34. Refer to the exhibit. VLAN 10 has been configured on the VTP server. Users who are assigned to VLAN 10 are connected as shown in the exhibit. On the basis of the outputs that are provided, which group of users will be able to communicate with the users on VLAN 10 on SW1? all the users who are connected only to SW2 users on VLAN 10 who are connected only to SW3 users on VLAN 10 who are connected only to SW4 users on VLAN 10 who are connected to both SW3 and SW4 35. Refer to the exhibit. Which three options correctly identify information that could be associated with this output?(Choose three.) Interface FastEthernet3/0/0 is subinterfaced. A non-proprietary trunking protocol is in use. The configuration is appropriate for a router-on-a-stick network design. A shutdown command has been applied to interface FastEthernet3/0/0. Interface FastEthernet3/0/0.3 is mapped to the default management VLAN. An IP address should be applied to FastEthernet3/0/0 for correct data routing. 36. Refer to the exhibit. The Layer 2 switching design that is shown has been implemented in a campus environment that is using Spanning Tree Protocol. All inter-switch links that are shown are trunks. Whenever an inter-switch link fails, the network takes nearly a minute to completely converge. How can the convergence time be reduced? Increase the capacity of the distribution and core trunk links to 10 Gb/s. Add a trunk link that directly connects D1 and D2. Use Layer 3 switching on the core switch. Implement Rapid Spanning Tree Protocol. 37. Refer to the exhibit. Each switch is configured to participate in STP for VLANs 1, 10, 20, and 30. Which switch will become the root for VLAN 20? A B C D 38. Refer to the exhibit. Switches S2 and S3 are properly connected using an ethernet cable. A network administrator has configured both switches with VTP, but S3 is unable to propagate VLANs to S2. What could be the reason for this? The VTP configuration revision is different on both switches. The VTP domains are different on both switches. VTP pruning is disabled. VTP v2 is disabled. 39. In a three-layer hierarchical network design, which distribution layer function delineates broadcast domains? routing between VLANs aggregating traffic flows providing redundant links reducing the network diameter 40. Which parameter is used to uniquely identify one wireless network from another? SSID OFDM WEP DSSS 41. What is one disadvantage that 802.11a wireless has compared to 802.11g? Use of the 5GHz band requires much larger antennas. The OFDM modulation technique results in a slower data rate. There are fewer non-overlapping channels available to help reduce RF interference. The use of higher frequencies means that signals are more likely to be obstructed. 42. Which three statements are correct concerning the default configuration of a new switch? (Choose three.) It is configured in VTP server mode. STP is automatically enabled. The first VTY line is automatically configured to allow remote connections. VLAN1 is configured with a management IP address. All switch ports are assigned to VLAN1. The enable password is configured as cisco. 43. Refer to the exhibit. How is port Gi1/1 on SWT-A functioning in the spanning-tree topology? It is sending and receiving data frames. It is receiving BPDUs, but not sending data frames. It is participating in the election process by forwarding the BPDUs it receives. It is receiving BPDUs and populating the MAC address table, but not sending data. 44. While configuring a new switch, a network administrator configures the switch as an HTTP server. What benefits does this configuration provide? This allows the switch to host web pages for the network. This allows remote VPN connections to the switch over the Internet. This is required if a web server or web farm is attached to the switch. This allows web-based configuration tools to be used with the switch. 45. Which statement describes the use of voice VLANs in Cisco IP telephony? The voice VLAN carries both tagged and untagged traffic. The voice VLAN carries untagged traffic having special QoS markings. The voice VLAN must be configured on the switch port to which the IP phone attaches. Data and voice frames are tagged with same VLAN ID between the IP phone and the switch when a voice VLAN is configured. 46. Refer to the exhibit. If switch SW1 is configured with the four VLANs as shown in the exhibit, how many physical interfaces are needed on router R1 to configure inter-VLAN routing using subinterfaces? zero one two four 47. Refer to the exhibit. What does the term DYNAMIC indicate in the output that is shown? This entry can only be removed from the MAC address table by a network administrator. When forwarding a frame to the device with address 0060.5c5b.cd23, the switch does not have to perform a lookup to determine the final destination port. Only the device with MAC address 0060.5c5b.cd23 will be allowed to connect to port Fa0/18. The switch learned this MAC address from the source address in a frame received on Fa0/18. 48. Refer to the exhibit. The VTP domain has been configured as shown in the exhibit. The network technician accidentally configured the VTP server as a VTP client. After the technician reloaded the switches, all users in the VTP domain started to complain that they lost connectivity to the users on the same VLANs that are connected to other switches. What should be done in the future to prevent losing all VLAN configurations in a VTP domain? Configure all switches in VTP transparent mode and copy the VLAN configuration into flash. Configure all switches in the network as VTP clients and copy the VLAN configuration into NVRAM. Create a new domain and configure a second switch as a VTP server to take over in case of a primary VTP server failure. In the same domain, configure a second switch as a VTP server to take over in case of a primary VTP server failure. 49. Refer to the exhibit. How does SW1 manage traffic coming from Host A? SW1 drops the traffic because it is untagged. SW1 leaves the traffic untagged and forwards it over the trunk. SW1 tags the traffic with the lowest VLAN ID value and forwards it over the trunk link. SW1 encapsulates the traffic with 802.1Q encapsulation and forwards it over the trunk link. 50. An administrator is troubleshooting a PC on the network which is suffering from slow and intermittent connectivity. The PC has a ping success rate to the default gateway of less than half the ping attempts. Other PCs on the switch can consistently ping the default gateway. The switch port is configured for auto duplex and the PC is configured for full duplex. What will commonly cause this problem? The PC is set to full duplex. The switch port fails to autonegotiate the duplex setting and defaults to half duplex, which causes a duplex mismatch. The switch traffic is exceeding available frame buffers. The result is that frames are being dropped. The PC and the default gateway have different bandwidth Ethernet ports. The default gateway is not on the same switch that the PC is. 51. Refer to the exhibit. A network administrator has segmented the network into two VLANs and configured Router1 for inter-VLAN routing. A test of the network, however, shows that hosts on each VLAN can only access local resources and not resources on the other VLAN. What is the most likely cause of this problem? Switch port Fa0/1 is not trunking. Router interface Fa0/0 is possibly down. No routing protocol is configured on Router1. One of the router subinterfaces is possibly down. 52. What impact does the use of the mdix auto configuration command have on an Ethernet interface on a switch? automatically detects duplex settings automatically detects interface speed automatically detects copper cable type automatically assigns the first detected MAC address to an interface | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Posted: 05 Oct 2010 07:03 AM PDT
One often get confused between a routing protocol and a routed protocol. A routing protocol such as RIP is used to route information packets over the Internet, where as a routed protocol such as IP (or IPX) is the payload (contains data) that get routed from source to the destination. Routing protocols are primarily distinguished into three types:
The table below provides the routing protocol used with different routed protocols:
Routing Metric: This is a fundamental measure that routing protocols use for determining appropriate route to deliver packets. Each routing protocol uses its own measure of metric, and a sample of routing metrics used by different routing protocols is given below:
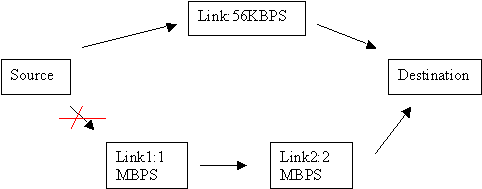 The RIP routed packets take the path through 56KBPS link since the destination can be reached in one hop. Though, the alternative provides a minimum bandwidth of 1MBPS (though using two links of 1MBPS, and 2MBPS each), it represents 2 hops and not preferred by the RIP protocol. Link State vs. Distance VectorDistance Vector routing protocols usually send their entire routing table to their nearest neighbors at regular intervals. A router that receives several such routing tables filter the routes and arrive at its own and retransmits it to its neighbouring routers. There will some period of time where different routers hold non-optimized routes initially. After some time, known as convergence time, a final routing table is arrived at by all the routers. A faster convergence time results in a stable network.RIP, as mentioned earlier uses hop count as the metric for computing a route to a given destination. Other Distance Vector routing protocols, such as IGRP, improve on this by using hop count, bandwidth, current load, cost, and reliability to determine the best path. Link State routing protocols usually send only the routing changes to every other router within their area. Unlike Distance Vector, routers using Link State routing protocols maintain a picture of the entire network. A router can use this network wide information to determine the best route for traffic. Example Question: What is true about IP routing? A. The frame changes at each hop B. The source IP address changes at each hop C. The destination IP address changes at each hop D. The hardware interface addresses remain constant Correct answer: A Explanation: IP Packets are transported from source network to the destination network by what is known as routing. Hop-by-hop routing model is used by the Internet for delivery of packets. At each hop, the destination IP address is examined, the best next hop is determined by the routing protocol (such as RIP, OSPF or BGP) and the packet is forwarded by one more hop through this route. The same process takes place at the next hop. During this process, the logical addresses remain same. In an IP network, the logical addresses are IP addresses. The hardware interface addresses, such as MAC address change with each hop. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Posted: 28 Oct 2010 08:50 AM PDT 1. Refer to the exhibit. What is the correct destination socket number for a web page request from Host A to the web server? 00-08-a3-b6-ce-46 198.133.219.25:80 C 198.133.219.0/24 is directly connected, FastEthernet0/0 2. Which prompt represents the appropriate mode used for the copy running-config startup-config command ? Switch-6J> Switch-6J# Switch-6J(config)# Switch-6J(config-if)# Switch-6J(config-line)# 3. Due to a security violation, the router passwords must be changed. What information can be learned from the following configuration entries? (Choose two) Router(config)# line vty 0 3 Router(config-line)# password c13c0 Router(config-line)# login The entries specify three Telnet lines for remote access. The entries specify four Telnet lines for remote access. The entries set the console and Telnet password to "c13c0″. Telnet access will be denied because the Telnet configuration is incomplete. Access will be permitted for Telnet using "c13c0″ as the password. 4. Refer to the exhibit. Each media link is labeled. What type of cable should be used to connect the different devices? Connection 1 – rollover cable Connection 2 – straight-through cable Connection 3 – crossover cable Connection 1 – crossover cable Connection 2 – rollover cable Connection 3 – crossover cable Connection 1 – straight-through cable Connection 2 – crossover cable Connection 3 – crossover cable Connection 1 – straight-through cable Connection 2 – crossover cable Connection 3 – straight-through cable Connection 1 – crossover cable Connection 2 – straight-through cable Connection 3 – crossover cable 5. Refer to the exhibit. What function does router RT_A need to provide to allow Internet access for hosts in this network? address translation DHCP services ftpd web server 6. When connectionless protocols are implemented at the lower layers of the OSI model, what is usually used to acknowledge that the data was received and to request the retransmission of missing data? IP UDP Ethernet a connectionless acknowledgement an upper-layer, connection-oriented protocol or service 7. Refer to the exhibit. Host A is transmitting data to host B. What addresses will host A use to for the destination IP and MAC addresses in this communication? Destination MAC: BBBB:BBBB:BBBB Destination IP: 172.22.0.62 Destination MAC: DDDD:DDDD:DDDD Destination IP: 172.22.0.75 Destination MAC: EEEE:EEEE:EEEE Destination IP: 172.22.0.62 Destination MAC: BBBB:BBBB:BBBB Destination IP: 172.22.0.75 Destination MAC: EEEE:EEEE:EEEE Destination IP: 172.22.0.75 Destination MAC: DDDD:DDDD:DDDD Destination IP: 172.22.0.94 8. Refer to the exhibit. Cable 1 and cable 2 have the ends wired for specific physical layer requirements. The table lists each segment by number and the cable which has been installed by the network technician between the network components on that segment. From the data given, which segments have the correct cable installed? (Choose three.) segment1 segment2 segment3 segment4 segment5 9. What is true regarding network layer addressing? (Choose three) uses a flat structure prevent broadcasts heirarchical uniquely identifies each host 48 bits in length contains a network portion 10. Refer to the exhibit. What two facts can be determined about the exhibited topology? (Choose two) A single broadcast domain is present Two logical address ranges are required. Three broadcast domains are shown. Four networks are needed. Five collision domains exist. 11. Refer to the exhibit. What two facts can be determined from the information that is given? (Choose two.) This exchange is part of the three-way handshake. The source port indicates that a Telnet session has been initiated. The data is flowing from server to client. The destination port indicates that an HTTP session has been initiated. The data listed is associated with the transport layer. The source port does not support communication with the destination port that is listed. 12. In a Cisco IOS device, where is the startup-configuration file stored? Flash NVRAM RAM ROM 13. Refer to the exhibit. The network containing router B is experiencing problems. A network associate has isolated the issue in this network to router B. What action can be preformed to correct the network issue? issue the clock rate command on interface Serial 0/0/0 issue the description command on interface Serial 0/0/1 issue the ip address command on interface FastEthernet 0/0 issue the no shutdown command on interface FastEthernet 0/1 14. Refer to the exhibit. A technician is working on a network problem that requires verification of the router LAN interface. What address should be pinged from this host to confirm that the router interface is operational? 127.0.0.1 192.168.64.196 192.168.254.1 192.168.254.9 192.168.254.254 15. Which combination of network id and subnet mask correctly identifies all IP addresses from 172.16.128.0 through 172.16.159.255? 172.16.128.0 255.255.255.224 172.16.128.0 255.255.0.0 172.16.128.0 255.255.192.0 172.16.128.0 255.255.224.0 172.16.128.0 255.255.255.192 16. Refer to the exhibit. Host A attempts to establish a TCP/IP session with host C. During this attempt, a frame was captured with the source MAC address 0050.7320.D632 and the destination MAC address 0030.8517.44C4. The packet inside the captured frame has an IP source address 192.168.7.5, and the destination IP address is 192.168.219.24. At which point in the network was this packet captured? leaving host A leaving ATL leaving Dallas leaving NYC 17. Refer to the exhibit. The diagram represents the process of sending email between clients. Select the list below that correctly identifies the component or protocol used at each numbered stage of the diagram. 1.MUA 2.MDA 3.MTA 4.SMTP 5.MTA 6.POP 7.MDA 8.MUA 1.MUA 2.POP 3.MDA 4.SMTP 5.MTA 6.MDA 7.SMTP 8.MUA 1.MUA 2.POP 3.SMTP 4.MDA 5.MTA 6.SMTP 7.POP 8.MUA 1.MDA 2.SMTP 3.MTA 4.SMTP 5.MTA 6.MUA 7.POP 8.MDA 1.MUA 2.SMTP 3.MTA 4.SMTP 5.MTA 6.MDA 7.POP 8.MUA 18. Refer to the exhibit. The command that is shown was issued on a PC. What does the IP address 192.168.33.2 represent? IP address of the host default gateway of the host IP address of the homepage for the host primary domain name server for the host IP address of the website resolver1.mooki.local 19. Refer to the exhibit. On the basis of the IP configuration that is shown, what is the reason that Host A and Host B are unable to communicate outside the local network? Host A was assigned a network address. Host B was assigned a multicast address. Host A and Host B belong to different networks. The gateway address was assigned a broadcast address. 20. Refer to the exhibit. The tracert command is initiated from PC1 to PC4. Which device will send a response to the initial tracert packet from PC1? Athens Ankara London Paris PC4 21. Which password is automatically encrypted when it is created? vty aux console enable secret enable password 22. Which OSI layer does IP rely on to determine whether packets have been lost and to request retransmission? application presentation session transport 23. Refer to the exhibit. Which two statements describe the information that is represented in the header? (Choose two) This is a server response. The UDP protocol is being used. The destination port indicates a Telnet session. The return segment will contain a source port of 23. The next session originated from the client of this session will use the source port number 13358. 24. The Layer 4 header contains which type of information to aid in the delivery of data? service port number host logical address device physical address virtual connection identifier 25. As network administrator, what is the subnet mask that allows 510 hosts given the IP address 172.30.0.0? 255.255.0.0 255.255.248.0 255.255.252.0 255.255.254.0 255.255.255.0 255.255.255.128 26. When must a router serial interface be configured with the clock rate command? when the interface is functioning as a DTE device when the interface timers have been cleared when the connected DTE device is shut down when the interface is functioning as a DCE device 27. Refer to the exhibit. What is required on host A for a network technician to create the initial configuration on Router1? an FTP client a Telnet client a terminal emulation program a web browser 28. Refer to the exhibit. Which set of devices contains only intermediary devices? A, B, D, G A, B, E, F C, D, G, I G, H, I, J 29. Refer to the exhibit. A network technician is trying to determine the correct IP address configuration for Host A. What is a valid configuration for Host A? IP address: 192.168.100.19; Subnet Mask: 255.255.255.248; Default Gateway: 192.16.1.2 IP address: 192.168.100.20; Subnet Mask: 255.255.255.240; Default Gateway: 192.168.100.17 IP address: 192.168.100.21; Subnet Mask: 255.255.255.248; Default Gateway: 192.168.100.18 IP address: 192.168.100.22; Subnet Mask: 255.255.255.240; Default Gateway: 10.1.1.5 IP address: 192.168.100.30; Subnet Mask: 255.255.255.240; Default Gateway: 192.168.1.1 IP address: 192.168.100.31; Subnet Mask: 255.255.255.240; Default Gateway: 192.168.100.18 30. A routing issue has occurred in you internetwork. Which of the following type of devices should be examined to isolate this error? access point host hub router switch 31. Which type of media is immune to EMI and RFI? (Choose two.) 10 Base-T 10 Base-2 10 Base-5 100 Base-FX 100 Base TX 1000 Base LX 32. Refer to the exhibit. With the router running NAT, what IP addresses can be applied to the computer to allow access to the Internet? (Choose three) 192.168.18.38 192.168.18.48 192.168.18.49 192.168.18.52 192.168.18.59 192.168.18.63 33. Which three IPv4 addresses represent a broadcast for a subnet? (Choose three.) 172.16.4.63 /26 172.16.4.129 /26 172.16.4.191 /26 172.16.4.51 /27 172.16.4.95 /27 172.16.4.221 /27 34. Refer to the exhibit. Assume all devices are using default configurations. How many subnets are required to address the topology that is shown? 1 3 4 5 7 35. What are three characteristics of CSMA/CD? (Choose three) Devices can be configured with a higher transmission priority. A jam signal indicates that the collision has cleared and the media is not busy. A device listens and waits until the media is not busy before transmitting. The device with the electronic token is the only one that can transmit after a collision. All of the devices on a segment see data that passes on the network medium. After detecting a collision, hosts can attempt to resume transmission after a random time delay has expired. 36. A technician is asked to secure the privileged EXEC mode of a switch by requiring a password. Which type of password would require this login and be considered the most secure? console enable enable secret VTY 37. A PC can not connect to any remote websites, ping its default gateway, or ping a printer that is functioning properly on the local network segment. Which action will verify that the TCP/IP stack is functioning correctly on this PC? Use the ipconfig /all command at the host's command prompt. Use the ping 127.0.0.1 command at the command prompt. Use the traceroute command at the command prompt to identify any failures on the path to the gateway. Use FTP to check for connectivity to remote sites. Download a troubleshooting tool from the PC manufacturer's website. 38. Refer to the exhibit. When computer A sends a frame to computer D, what computers receive the frame? only computer D only computer A and computer D only computer B, computer C, and computer D all computers 39. Examine the graphic with current configurations. Host A in the Clerical offices failed and was replaced. Although a ping to 127.0.0.1 was successful, the replacement computer can not access the company network. What is the likely cause of the problem? IP address incorrectly entered network cables unplugged subnet mask incorrectly entered network card failure 40. Which two functions of the OSI model occur at layer two? (Choose two.) physical addressing encoding routing cabling media access control 41. Refer to the exhibit. A router, whose table is shown, receives a packet that is destined for 192.168.1.4. How will router treat the packet? The packet will be dropped. The packet will be forwarded via FastEthernet 0/0. The packet will be forwarded to the destination host. The packet will be forwarded to the 192.168.1.3 next-hop address. 42. Which range of port numbers are reserved for services that are commonly used by applications that run on servers? 0 to 255 0 to 1023 1024 to 49151 49152 to 65535 43. Refer to the exhibit. What three statements are true about the IP configuration that is shown? (Choose three.) The address that is assigned to the computer represents private addressing. The computer is unable to communicate outside of the local network. The network of this computer can have 126 hosts. The prefix of the computer address is /27. The IP address that is assigned to the computer is routable on the Internet. The IP address that is assigned to the computer is a broadcast address. 44. Refer to the exhibit. A network administrator remotely accesses the CLI of RouterB from PC1 using Telnet. Which statement is true about this connection? The data is automatically encrypted. A Telnet server process is running on PC1. The connection is made through a VTY session on the router. A GET request was sent to RouterB to retrieve data during this session. 45. Which three statements characterize the transport layer protocols? (Choose three.) TCP and UDP port numbers are used by application layer protocols. TCP uses port numbers to provide reliable transportation of IP packets. UDP uses windowing and acknowledgments for reliable transfer of data. TCP uses windowing and sequencing to provide reliable transfer of data. TCP is a connection-oriented protocol. UDP is a connectionless protocol. 46. Which of the following are the address ranges of the private IP addresses? (Choose three.) 10.0.0.0 to 10.255.255.255 200.100.50.0 to 200.100.25.255 150.150.0.0 to 150.150.255.255 172.16.0.0 to 172.31.255.255 192.168.0.0 to 192.168.255.255 127.16.0.0 to 127.31.255.255 47. Which OSI layers offers reliable, connection-oriented data communication services? application presentation session transport network 48. Refer to the exhibit. Which logical topology best describes the exhibited network? star ring point-to-point multiaccess mesh 49. During the encapsulation process, which identifiers are added at the transport layer? two networks routing the packets two applications communicating the data two hosts at either end of the communication two nodes on the local network exchanging the frame 50. What are two characteristics of the data link layer? (Choose two.) It segments and reorders the data. It exchanges the frames between nodes. It defines the method by which network devices place data onto the media. It manages the transfer of data between the processes that run on each host. It retrieves signals from the media and restores them to their bit representations. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Posted: 19 Feb 2010 09:55 PM PST Thanks IS_IS eigrp! This is Final exam (French), if you have other test, please send to me at nguyenhuuhai.it@gmail.com thanks. Download now | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Posted: 30 Sep 2010 06:38 AM PDT
For example, using our test IP address and the default Class C subnet mask, we get: 192.189.210.078: 1100 0000.1011 1101.1101 0010.0100 1110 Class C IP Address 255.255.255.000: 1111 1111.1111 1111.1111 1111.0000 0000 Default Class C subnet mask 192.189.210.0 1100 0000 1011 1101 1101 0010 0000 0000 As can be seen above, by using and AND operator, we can compute the network portion of an IP address. The network portion for the IP address given in the above example is 192.189.210.0, and the host portion of the IP address is 078. Given below is a table that provides binary equivalent of decimal values. For binary conversion, take first octet of a given IP address (in dotted decimal form), and lookup the binary value. Then take the second octet and lookup the binary value, and so on. Binary Conversion Table
Example Question: Which of the following is a Class C IP address?
Correct Answer: D. Explanation: IP addresses are written using decimal numbers separated by decimal points. This is called dotted decimal notation of expressing IP addresses. The different classes of IP addresses is as below:
Network address of all zeros means "This network or segment". Network address of all 1s means " all networks", same as hexadecimal of all Fs. Network number 127 is reserved for loopback tests. Host (Node) address of all zeros mean "This Host (Node)". Host (Node) address of all 1s mean "all Hosts (Nodes) " on the specified network. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| CCNA Wireless - Any netsims available? Posted: 28 Sep 2010 08:23 AM PDT Hi, I am a CCNA and looking to recertify by taking the CCNA Wireless concentration as I would like to add some new knowlegde rather than just retake the current CCNA. I will need to know how to configure Cisco WCS, WLC's and AP's for the exam, so I am looking for a netsim like Boson's but for the Wireless config's only. Does a netsim for CCNA Wireless exist and if so what is it and how do I get it? Thanks. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Posted: 16 Jan 2010 05:35 AM PST Begin the test Read the question and then click on the checkbox that contains the correct answer(s). The small field to the immediate right of the question will either display "Yes" if you are correct or "No" if you have selected the wrong answer. Click on the "Explanation" button to find out more about the answer and click "Next Question" to continue the MCSE Practice test. Your answers are not graded, so keep track of the topics which with you had difficulty. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| You are subscribed to email updates from "Cisco" via Ehsan in Google Reader To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google Inc., 20 West Kinzie, Chicago IL USA 60610 | |












0 comments:
Post a Comment