Interop: Cyberwar test runs yield information about defenses |
- Interop: Cyberwar test runs yield information about defenses
- Offshoring: Preparing for India's Proposed Privacy Rules
- Facebook, Twitter need corporate security policies
- Cisco ASA Virtual Firewall Configuration
- Startup rolls out 40G data center switches at Interop
- Is OpenFlow a go?
- Integrated identity management: How to get it?
- Top 5 things to do before buying more security technology
- Little new in Obama cybersecurity proposal
- Adobe Flash update puts users in charge of privacy
- Facebook tightens log-in verification
- Unchecked usage can kill cost benefits of cloud services
- White House delivers cybersecurity legislation
- Caught! Facebook admits running anti-Google campaign
- Google jumps gun, adds new Flash Player to Chrome
- As 'big data' grows, IT job roles, technology must change
| Interop: Cyberwar test runs yield information about defenses Posted: 13 May 2011 08:32 AM PDT |
| Offshoring: Preparing for India's Proposed Privacy Rules Posted: 13 May 2011 08:00 AM PDT |
| Facebook, Twitter need corporate security policies Posted: 13 May 2011 06:13 AM PDT |
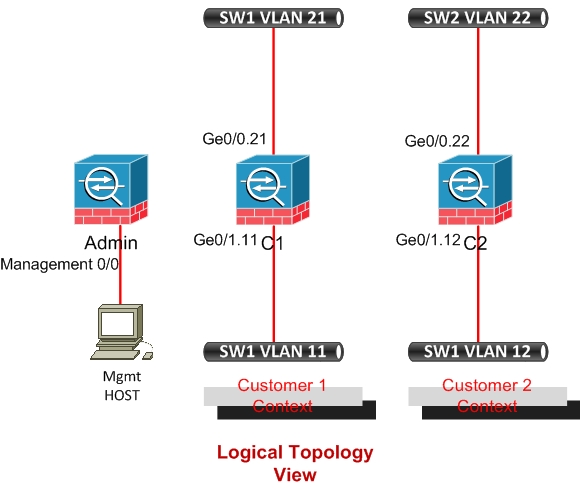
| Cisco ASA Virtual Firewall Configuration Posted: 13 May 2011 10:28 AM PDT Device virtualization is one of the most popular topics in IT industry today and Cisco has been supporting this concept in the majority of its network devices. In this article we will talk about Cisco ASA virtualization, which means multiple virtual firewalls on the same physical ASA chassis. Virtual ASA is also known as "Security Context". All firewall models (except ASA 5505) support multiple security contexts (i.e virtual firewalls). By default, all models support 2 security contexts without a license upgrade (except the ASA 5510 which requires the security plus license). Each Context has it's own configuration file and security policy, i.e. one context is completely isolated and does not depend on other contexts. The exception is the Admin Context, from which the whole ASA appliance (physical ASA) is managed and also is used to create the other Contexts. For enabling the creation of virtual contexts on the ASA appliance, we must switch to Multiple Context mode. In this mode some features are not available, like Dynamic Routing, IPSEC and SSL VPN, Multicast and Threat Detection. Let's make a little discussion when multiple context mode is advisable and when it is not. When would you want to use multiple security contexts? ● If you want to use the active/active failover feature. Keep in mind that with active/active failover, you should not use more than half of the available bandwidth. When should you not use multiple security contexts? ● If you need to provide VPN services such as remote access or site-to-site VPN tunnels. Now let's consider an example of how Contexts are configured. In the scenario in our topology below, we have one ASA appliance and let's create two contexts for two customers and one admin context for ASA appliance management. Physical Topology Diagram:
Logical Topology Diagram:
Equipment Used in this LAB ASA 5520 – Cisco Adaptive Security Appliance Software Version 8.0(3) Catalyst 2960 – LAN Lite IOS. Before starting configuration let's check if it works in Single context mode or multiple context mode. As I've already stated, ASA appliance must be in multiple context mode for creating Security contexts. !Verify ASA Operating mode. asa # show mode Security context mode: single
! enable multiple mode, for switching to this Mode, restart is required. asa(config)#mode multiple
Then the following output is displayed. ASA Appliance converts the current running configuration into two files: a new startup configuration that comprises the system configuration, and "admin.cfg" that comprises the admin context (stored in the root directory of the internal Flash memory). The original running configuration is saved as "old_running.cfg" (in the root directory of the internal Flash memory). WARNING: This command will change the behavior of the device The admin context configuration will be written to flash
The new running configuration file was written to flash
*** Rebooting…. !after rebooting verify ASA Operation mode asa# show mode After restarting let's start configuration of Contexts. First configure the admin context. !Configure the admin context !configure the Sub-interfaces for Customer1 !configure the Sub-interfaces for Customer2 Now we start creating contexts for Customer-1 and Customer-2 and allocate interfaces. ! Configure the Customer1 context shown as C1 in diagram. ! Configure the Customer2 context shown as C2 in diagram. I will not describe how VLANs on Switches are configured. Let's consider switching between Contexts. We can switch to any context from admin context, but we can't switch from Customers context to anywhere. ! Let's log in to Customer1 context. The syntax of command is the following: asa#changeto context c1 ! Let's switch to system configuration mode. Switching to this mode is available only from Admin Context. In system configuration mode Contexts are created and resources are allocated. asa#changeto system |
| Startup rolls out 40G data center switches at Interop Posted: 13 May 2011 07:16 AM PDT |
| Posted: 13 May 2011 06:57 AM PDT |
| Integrated identity management: How to get it? Posted: 13 May 2011 03:00 AM PDT |
| Top 5 things to do before buying more security technology Posted: 13 May 2011 03:00 AM PDT |
| Little new in Obama cybersecurity proposal Posted: 13 May 2011 02:10 AM PDT |
| Adobe Flash update puts users in charge of privacy Posted: 12 May 2011 03:38 AM PDT |
| Facebook tightens log-in verification Posted: 12 May 2011 02:24 AM PDT |
| Unchecked usage can kill cost benefits of cloud services Posted: 12 May 2011 01:36 AM PDT |
| White House delivers cybersecurity legislation Posted: 11 May 2011 11:20 PM PDT The White House today sent its cybersecurity legislation to Capitol Hill, asking for changes in the law that will give the Dept. of Homeland Security more authority and duties in overseeing both private-sector and government networks. The White House is also asking for a national data-breach law that would supercede the patchwork of state data-breach laws now in place around the country. |
| Caught! Facebook admits running anti-Google campaign Posted: 11 May 2011 11:14 PM PDT |
| Google jumps gun, adds new Flash Player to Chrome Posted: 11 May 2011 11:14 PM PDT |
| As 'big data' grows, IT job roles, technology must change Posted: 11 May 2011 10:43 PM PDT |
| You are subscribed to email updates from "Cisco" via Ehsan in Google Reader To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google Inc., 20 West Kinzie, Chicago IL USA 60610 | |













0 comments:
Post a Comment