Network Security Notes: Cisco Network Security Certification Training |
- Network Security Notes: Cisco Network Security Certification Training
- Network Security Notes: Network Protocols: Configuring EIGRP Authentication Protocol
- Extreme looks to one-up Cisco, others in data center
- Most companies skimp on third-party code checks, study finds
- India defends right to access personal data
- Got SCIM?
- Data center anti-DDoS package on tap from Arbor
- Sony reported to be considering bounty for PSN attack
- NASA, Stanford websites hit by search engine scammers
- Privacy groups support new do-not-track bill
- Skype patches 'wormable' Mac bug
- Security firm exploits Chrome zero-day to hack browser, escape sandbox
- Vendors patch firewalls after controversial NSS Labs test
- WebGL hit by hard-to-fix browser security flaw
- HP counters Cisco with new switches, architecture
| Network Security Notes: Cisco Network Security Certification Training Posted: 10 May 2011 09:24 PM PDT I have archived few certificates related to Microsoft like MCSA 2003, MCSE 2003 and Cisco like CCNA. But in my future I want to gain more certificates of CISCO related to network security like Cisco IOS Security, Adaptive Security Appliance, VPN 3000 Concentrator, Network Intrusion Detection, Host Intrusion Detection, End-to-End Security Implementation... * Cisco IOS Security: Securing Networks with Cisco Routers and Switches (SNRS), Network Administration Control (NAC), Securing Cisco Routers (SECR) * Adaptive Security Appliance: Securing Networks with PIX and ASA (SNPA) * VPN 3000 Concentrator: Cisco Secure Virtual Networks (CSVPN) * Network Intrusion Detehttp: Implementing Cisco Intrusion Prevention System (IPS) * Host Intrusion Detection: Securing Hosts Using Cisco Security Agent (HIPS) * End-to-End Security Implementation: Securing Cisco Network Devices (SND) I am really want to gain more certificates related to CISCO Network Security! But now I need to earn more money to get training and to do examination to complete the test requirements.... For more details about the Network Security Certification Training , please visit here... |
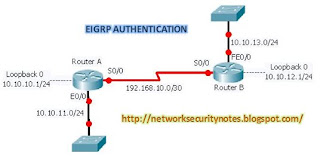
| Network Security Notes: Network Protocols: Configuring EIGRP Authentication Protocol Posted: 10 May 2011 08:19 PM PDT As my previous post about Understanding EIGRP protocol, this post I would like to share you about configuring EIGRP Authentication....
EIGRP authentication of packets has been supported since IOS version 11.3. EIGRP route authentication is similar to RIP version 2, but EIGRP authentication supports only the MD5 version of packet encryption. EIGRP's authentication support may at first seem limited, but plain text authentication should be configured only when neighboring routers do not support MD5. Because EIGRP is a proprietary routing protocol developed by Cisco, it can be spoken only between two Cisco devices, so the issue of another neighboring router not supporting the MD5 cryptographic checksum of packets should never arise. The steps for configuring authentication of EIGRP updates are similar to the steps for configuring RIP version 2 authentication: 1. Define the key chain using the command key−chain < name> in global configuration mode. This command transfers you to the key chain configuration mode. 2. Specify the key number with the key command in key chain configuration mode. You can configure multiple keys. 3. For each key, identify the key string with the key−string command. 4. Optionally, you can configure the period for which the key can be sent and received. Use the following commands: accept−lifetime {infinite|end−time|duration −seconds} send−lifetime {infinite|end−time|duration seconds} 5. Exit key chain configuration mode with the exit command. 6. Under interface configuration mode, enable the authentication of EIGRP updates with this command: ip authentication key−chain eigrp 7. Enable MD5 authentication of EIGRP updates using the following command: ip authentication mode eigrp md5 With the command below shows you how Router A should be configured to authenticate updates from Router B using EIGRP MD5 authentication, Command Listing A: Router A's configuration with MD5 authentication:
And the next below command here shows the configuration for Router B. Command Listing B: Router B's configuration with MD5 authentication: key chain router−b The Command Listing A configures Router A with a key chain value of router−a, a key value of 1, and a key−string value of eigrp. The Command Listing B configures Router B with a key chain value of router−b, a key value of 1, and a key−string value of eigrp. Notice again that the key chain need not match between routers; however, the key number and the key string associated with the key value must match between routers configured to use that key value. Although debugging of encrypted EIGRP packets is somewhat limited, a few commands can be used to verify that packet encryption is taking place correctly. Two of those commands are debug eigrp packet and show ip route. The debug eigrp packet command informs you if the router has received a packet with the correct key value and key string. The output of issuing this command can be seen here: Router−A#debug eigrp packet Router A is receiving MD5−authenticated packets from it neighbor, Router B. However, we cannot fully determine whether or not the authentication is taking place correctly without issuing the show ip route command on Router A. This allows us to look at the route table and determine that packet authentication is taking place correctly because the routes that Router B has sent to Router A are installed into the route table. Listing 1.7 displays the output of the show ip route command. Listing Command C: Route table of Router A with correct authentication configured: Router−A#sh ip route You can change Router A's key−string value for key 1 to see what kind of an effect this will have. The following lines will change the key−string value for key 1 on Router A to ospf: Router−A#config t |













0 comments:
Post a Comment