Configuring EasyVPN Between Cisco Routers |
- Configuring EasyVPN Between Cisco Routers
- NSA wants bulletproof smartphone, tablet security
- IT admins gone wild: 5 rogues to watch out for
- Ready or not, they're already in your enterprise
- A new security architecture for the cloud
- Mesh networks may make SQL injection attacks more persistent
- Attackers exploit latest Flash bug on large scale, says researcher
- An update on security threats
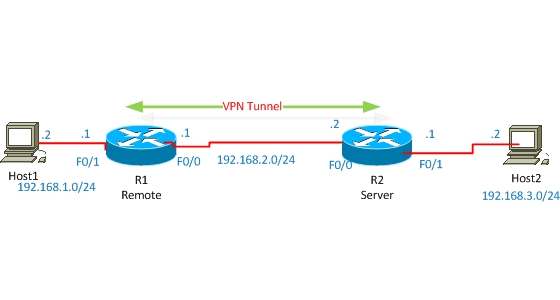
| Configuring EasyVPN Between Cisco Routers Posted: 20 Jun 2011 11:35 AM PDT Basically Cisco Easy VPN is usually used for Cisco easy VPN Client termination. In this post however, let's consider the configuration of Cisco Easy VPN between two Cisco routers. Just keep in mind that an EasyVPN scenario involves an EasyVPN Server and EasyVPN Remote Clients. The basic configuration is performed on the Cisco Easy VPN Server and the configuration done on Cisco Easy VPN Remote is almost similar to the configuration done on Cisco easy VPN client. Let's consider an example as shown on diagram below: configure R1 as an easy VPN Remote and configure R2 as an easy VPN Server and force the traffic to flow via the VPN Tunnel between the Loopback interfaces.
Before starting the Easy VPN configuration, check the connectivity between the Loopback interfaces. For simplicity I configured default route on both routers to each other. Now let's start configuration. First of all configure R2 as Easy VPN Server. R2 Configuration !enable AAA new-model ! enable local authentication method list with name userauthen for X-AUTH ! enable local authorization method list with name groupauthor for X-AUTH !create username, by which authorization of Easy VPN Remote will occur later. !create ISAKMP PHASE #1 Negotiation !Create group with pre-shared key for IKE authentication. Save-password Feature allows Remote to save password. !create IPSEC Transform-set for DATA Encryption !Create Dynamic-map , which will be used to crypto-map later. ! Create crypto map, which will be used to AAA authentication, authorization lists and also in dynamic-crypto map. !Now attach the crypto-map to outside interface. By this, easy vpn server configuration is completed. Now let's start Remote configuration. Configuration is almost similar to the Cisco Easy VPN Client configuration. R1 Configuration ! Create VPN Profile. ! Connect automatically to Easy VPN Server. If we don't do this, then we'll have to connect manually to Easy VPN server every time the network is down. ! Easy VPN group username and password, which are created on server. !Indicate Mode as network-extension. !Indicate the IP address of Easy VPN Server. ! Use Username and password saved in profile for connecting to Easy VPN Server. ! Save user and password in Profile. ! Determine Inside interface. Inside and outside interfaces must be determined on Easy VPN Remote. interface FastEthernet0/0 Both sites are completed now, so let's do some testing: R2#show crypto isakmp sa IPv4 Crypto ISAKMP SA R2#show crypto ipsec sa interface: Fastethernet 0/0 Crypto map tag: clientmap, local addr 192.168.2.2 protected vrf: (none) |
| NSA wants bulletproof smartphone, tablet security Posted: 20 Jun 2011 08:41 AM PDT |
| IT admins gone wild: 5 rogues to watch out for Posted: 20 Jun 2011 07:51 AM PDT |
| Ready or not, they're already in your enterprise Posted: 20 Jun 2011 05:36 AM PDT |
| A new security architecture for the cloud Posted: 20 Jun 2011 05:35 AM PDT |
| Mesh networks may make SQL injection attacks more persistent Posted: 20 Jun 2011 05:32 AM PDT |
| Attackers exploit latest Flash bug on large scale, says researcher Posted: 20 Jun 2011 02:55 AM PDT |
| Posted: 20 Jun 2011 09:00 AM PDT Each year several vendors and organizations publish updates on the state of the art in security threats. Most of these updates could be entitled "Be nervous, be very very nervous." While it is never fun to read these reports, they do provide helpful insight into vulnerabilities that we should be aware of. With that in mind, we will use this newsletter to highlight some of the findings of a recent IBM report on security threats. |
| You are subscribed to email updates from "Cisco" via Ehsan in Google Reader To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google Inc., 20 West Kinzie, Chicago IL USA 60610 | |












0 comments:
Post a Comment