Activeden – Universal Media Player |
- Activeden – Universal Media Player
- Private Vlan Configuration
- Lessons in security leadership: Jamil Farshchi
- Lessons in security leadership: Jennifer Bayuk
- Lessons in security leadership: David Komendat
- Lessons in security leadership: Dwaine Nichol
- Lessons in security leadership: Andy Ellis
- Taiwan political party accusses China of hacking
- VMware preparing data loss prevention features for vShield
- Quick Tip: Detect User Inactivity in a Flash Movie
- Creating a YouTube Search and Play Gadget with PureMVC
- Build a Simple Flash Frisbee Game With AS3
| Activeden – Universal Media Player Posted: 09 Aug 2011 04:54 PM PDT Player features Two skins: dark and light Advertise intro video Watermark logo Configurable quality for HD and LD resources Cover images Google Analytics integration Fullscreen Realtime resize YouTube features Individual Video IDs with XML override of title, description, thumbnail and cover image Individual Video IDs with all data fetched from YouTube YouTube playlist support... |
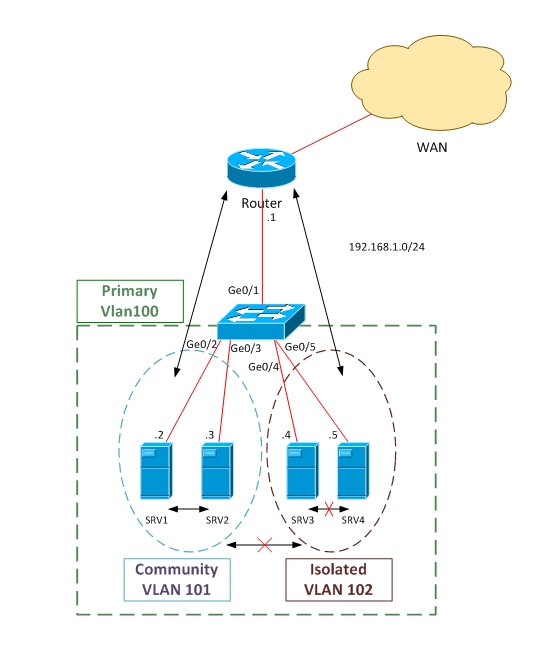
| Posted: 09 Aug 2011 12:23 PM PDT We know that a Layer 2 VLAN is an isolated Broadcast Domain and for communicating between VLANs a Layer 3 Device is required for inter-VLAN Routing. A Private VLAN gives us the opportunity to divide a VLAN into Sub VLANs. In the case of PVLAN, a normal VLAN is mapped on Secondary VLANs. This helps us to restrict devices being connected in the same normal VLAN (subnet) to communicate with each other. Catalyst 3560 and higher models support PVLAN. Often PVLANs are used in cases where servers are located in a DMZ on the same Layer2 Vlan and we want to restrict these servers to communicate between them. This helps a lot in security. If the servers are publicly accessible from the Internet, when one of the servers is compromised by hackers, we can block the attacker to access the other servers on the same Vlan. Of course we can do this with a L3 device or firewall, but in this case each server should have it's own VLAN and as a result we'll get a complex network. In the case of PVLAN, we'll have one network (VLAN) and we'll restrict the connection between servers by creating secondary VLANs. Private VLAN Types and Port Types: Promiscuous (P): Usually connects to a router (Default gateway) and also to span port – a type of a port which is allowed to send and receive frames from any other port on the Primary VLAN. Isolated (I): This type of port is only allowed to communicate with P-ports – they are "stub". This type of port usually connects to hosts. Only one isolated VLAN is created. The ports, which are in isolated VLAN, can communicate to each other. Community (C): The ports in the same Community can communicate with each other and also are connected to Promiscuous port. There are multiple Communities available. Community ports are allowed to talk to their buddies, sharing the same group (of course they can talk to P-ports). Let's see how to configure PVLANs Equipment Used in this LAB: Cisco Catalyst 3560 – C3560-IPSERVICES-M Version 12.2(50)SE
Scenario: Create one Community vlan, in which SRV1 and SRV2 will belong to. Create also an Isolated VLAN, in which SRV3 and SRV4 will belong to. Make Ge0/1 promiscuous and connect to default gateway (router). According to this configuration, SRV1 and SRV2 can talk to each other and also with Router (Default Gateway). On the other hand, Servers in Isolated VLAN (SRV3 and SRV4) will not communicate between each other and also will not be able to talk with F0/0 (Router-Default Gateway). Before starting PVLAN configuration, switching VTP Mode to Transparent is required. If VTP works in other mode, PVLAN will not work. !switch to Transparent mode Switch(config)# vtp mode transparent !Create Isolated VLAN Switch(config)# vlan 102 !create community vlan Switch(config)# vlan 101 Switch(config-vlan)#private-vlan community !Create Primary VLAN and map with secondary vlans Our Complete Configuration looks Like This: vlan 100 vlan 102 ! Create promiscuous port and map with the other vlans Switch(config)# interface ge0/1 ! association of Ge0/2 and Ge0/3 ports with Primary and Secondary VLANS. According to our scenario Ge0/2 and Ge0/3 should be in community Vlan. Switch(config)# interface range ge0/2-ge0/3 ! association Ge0/4 and Ge0/5 ports with Primary and Secondary VLANS. According to our !scenario Ge0/4 and Ge0/ should be in Isolated Vlan. Switch(config)# interface range ge0/4-ge0/5 Configuration is completed now so let's see how the output looks like. Switch# show interface status Port Name Status Vlan Duplex Speed Type |
| Lessons in security leadership: Jamil Farshchi Posted: 09 Aug 2011 06:49 AM PDT |
| Lessons in security leadership: Jennifer Bayuk Posted: 09 Aug 2011 06:44 AM PDT |
| Lessons in security leadership: David Komendat Posted: 09 Aug 2011 06:37 AM PDT |
| Lessons in security leadership: Dwaine Nichol Posted: 09 Aug 2011 06:34 AM PDT |
| Lessons in security leadership: Andy Ellis Posted: 09 Aug 2011 06:28 AM PDT |
| Taiwan political party accusses China of hacking Posted: 09 Aug 2011 02:16 AM PDT |
| VMware preparing data loss prevention features for vShield Posted: 08 Aug 2011 02:13 AM PDT |
| Quick Tip: Detect User Inactivity in a Flash Movie Posted: 08 Aug 2011 11:17 PM PDT |
| Creating a YouTube Search and Play Gadget with PureMVC Posted: 08 Aug 2011 11:24 PM PDT |
| Build a Simple Flash Frisbee Game With AS3 Posted: 08 Aug 2011 11:25 PM PDT |
| You are subscribed to email updates from "Cisco" via Ehsan in Google Reader To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google Inc., 20 West Kinzie, Chicago IL USA 60610 | |












0 comments:
Post a Comment